
Updated on: March 20, 2024
SafetyDetective’s research lab discovered a leak online that exposed an elastic server containing 3GB of data with over 1.6 million users affected. We informed the apparent owners of this database as soon as we were able to identify them. Because we did not receive a response from the owner of the database, we reached out to the hosting server company (Tata Communications), who subsequently closed the leak.
Editor’s Note: Tata Communications is not responsible for the data leak.
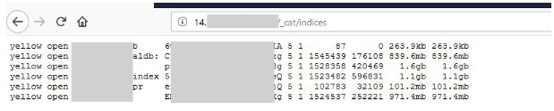
The Mumbai-based server seemed to be connected to the brand new Talanton.ai website, which as of publishing is not a functioning platform on the user-end. Talanton’s site is a job posting and searching platform based in India and specializing in professional, predominantly hitech job openings. It is part of a network of websites (jobyiee.com), including others related to job search and headhunting for candidates around the globe.
What’s Exposed?
The server was exposed between May 17, 2019 and June 15, 2019, from what Anurag Sen, a lead ethical hacker from our research team, was able to see (we discovered it on May 30, 2019). The database exposed personal contact information and other PII for employers and job seekers alike.
Note: The individuals listed in the database have been added through various methods of sourcing. Unless there is specific information regarding expected salary or similar, there is no way of distinguishing between the professionals who were added without their knowledge and those who actively participated in job seeking activities.
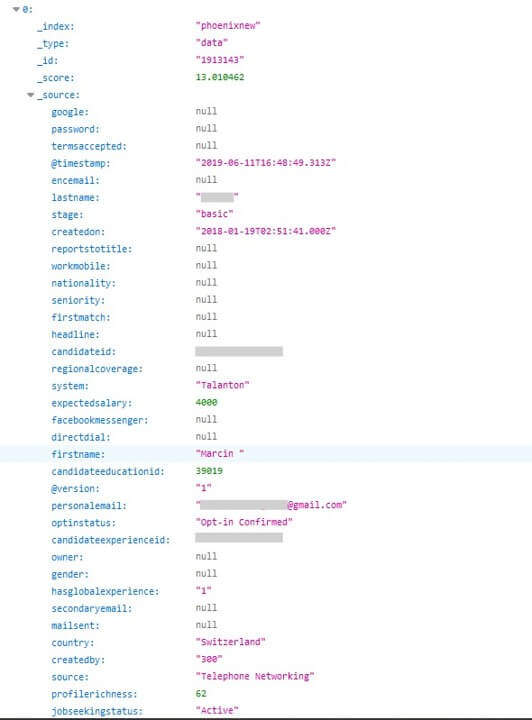
Information obtained by “telephone networking.”
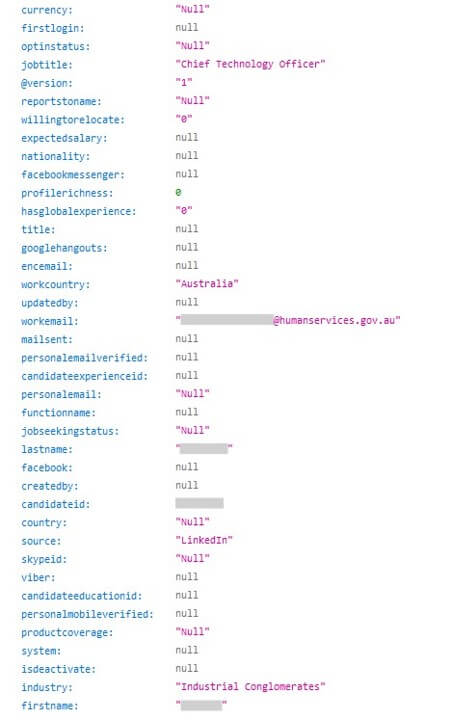
Many countries are represented in this exposure of professionals’ personal information, including the USA, India, Israel, UK, France, multiple additional European countries, Australia, UAE, Singapore, and Hong Kong, just to name a few. Also leaked are the direct numbers and emails of CISOs (Chief Information Security Officers), CEOs, and high-ranking government employees – including the CTO of the Australian government.
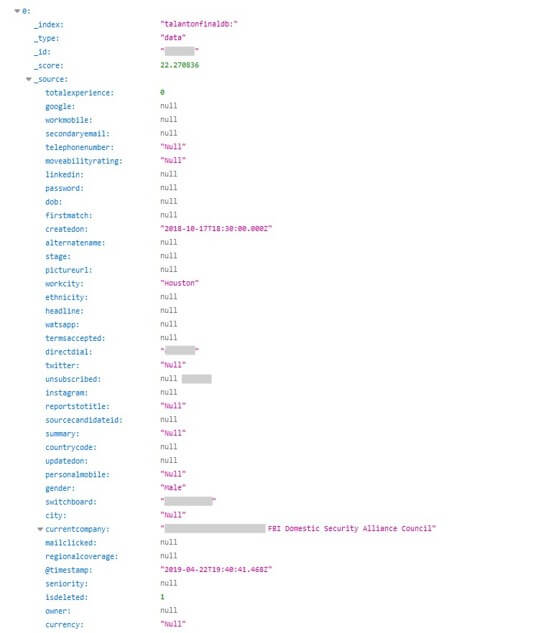
Even government security agencies, including the FBI, were not left out of this database – they were represented by the data of an FBI Domestic Security Alliance Council member as well.
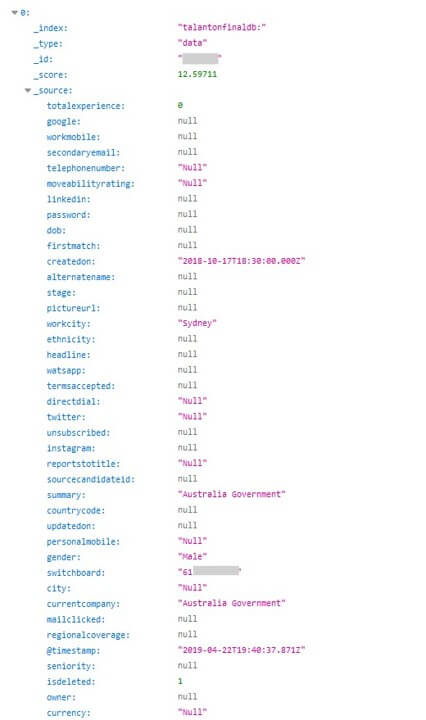
The information available about job seekers included direct phone numbers, locations, titles, current employers, salary expectations, personal email addresses, gender, nationality, job seeking status, and other similar – often private – information. Also included were the encrypted passwords of over 50,000 user records.
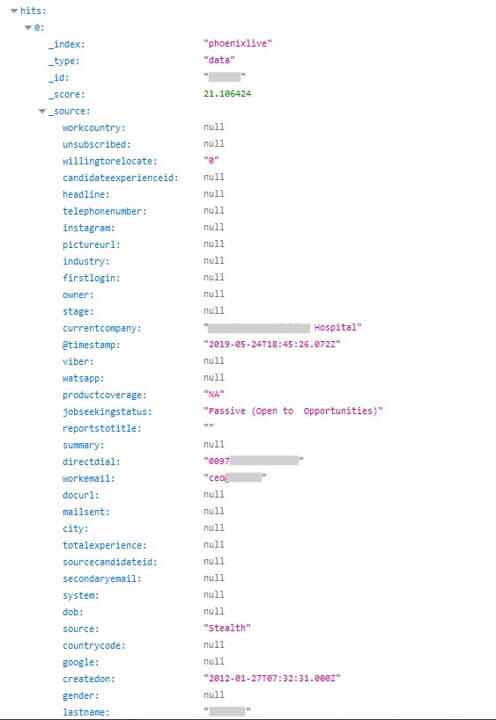
This CEO is open to opportunities.
For employers, the data leaked was similar. Private phone numbers, direct emails, salary information for specific positions, potentially otherwise undisclosed locations, and more of the like have been made available to the masses with this cybersecurity violation.
With ethnic background, gender, and other potentially sensitive information about high profile professionals, it may be possible for malefactors to utilize this as a method for blackmail, and they can also use this data for a mass phishing campaign. The impact of publicly disclosing private emails and mobile numbers – all of which appear to be accurate – can be severe, if used just so. In certain jurisdictions, this data can even be used as a tool for bribery and strong-arming.
While researching this database leak, we also stumbled across the details of Tommy Hilfiger Japan CEO, Tom Chu. You may remember a previous data breach we discovered earlier this year, where the Tommy Hilfiger Japan database exposed hundreds of thousands of customers to data theft.
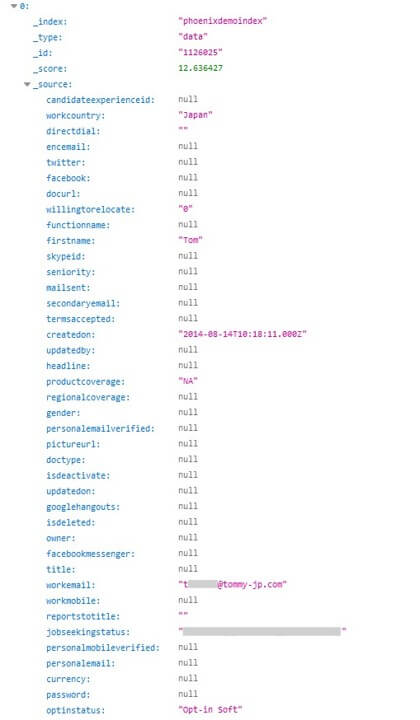
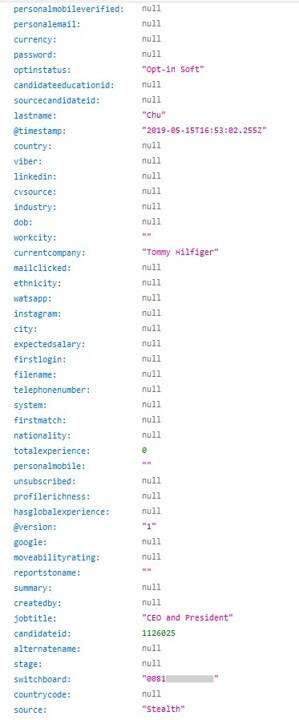
Preventing Data Exposure
How can you prevent your personal information from being exposed in a data leak and ensure that you’re not a victim of attacks if it is leaked?
- Be cautious of what information you give out and to whom
- Check that the website you’re on is secure (look for https and/or a closed lock).
- Only give out what you feel confident cannot be used against you (avoid government ID numbers, personal preferences that may cause you trouble if made public, etc.).
- Create secure passwords by combining letters, numbers, and symbols
- Do not click links in emails unless you are sure that the sender is legitimately who they represent themselves to be
- Double-check any social media accounts (even ones you no longer use) to ensure that the privacy of your posts and personal details are visible only to people you trust
- Avoid using credit card information and typing out passwords over unsecure WiFi networks
Find out more about the best tips to prevent phishing attacks, and how to avoid ransomware.
About Us
SafetyDetective.com is the world’s largest antivirus review website. The Safety Detective research lab is a pro bono service that aims to help the online community defend itself against cyber threats, while educating organizations on protecting their users’ data.
Published on: Jun 17, 2019