
Updated on: April 8, 2024
Short on Time? Here’s how to Protect Yourself from Phishing:
Phishing presents itself in many ways, from emails to phone calls to text messages. But it always works the same way; by attempting to lure you into performing a certain task with the appeal of something enticing – be it a free iPad or bucket loads of cash.
For phishing hackers, your ignorance is their bliss. Fortunately, because phishing scams require you to actually fall for them, if you’re aware of the problem, then it’s relatively easy to avoid them. So how do you go about identifying and avoiding phishing attacks? We’ll explain below…
What Is Phishing?

When we label types of malware, like viruses, spyware, or adware, we’re referring to the form the infection takes. Phishing is an exception to this rule as it describes how the problem happened, rather than how it behaves.
Phishing is successful when the victim clicks on a link or downloads a file, thereby unwillingly allowing the malicious software to infiltrate a device. Basically, phishing is an easy way for cybercriminals to steal your personal information, such as credit card numbers and account passwords, even if they don’t have the skillset to hack your network and steal that information. In most cases, scammers are able to convince or coerce their victims into giving over their information willingly.
It’s extremely important to protect your personal information, especially sensitive things like your Social Security number. SSNs are nearly impossible to replace, and once a scammer has yours, they can use it indefinitely for a wide variety of crimes.
How Does Phishing Work?
Phishers may contact you through a fraudulent email, phone call, or a fake website. They often disguise themselves as reputable companies, such as a bank, cell phone service providers, or a social media account or website for a major brand, and try to persuade you into divulging your personal information.
They are often trying to collect personal details like your address, credit card number, passwords, phone numbers, and even your insurance numbers.
Generally, phishers will claim the victim has won something, they are missing out on a limited-time deal or they are facing a final warning that an account will be removed if he or she does not enter their login credentials.
Here’s an example:
Say you receive an email from Amazon, a site you visit frequently for online shopping. The email is actually fake, but you don’t realize it at first. After all, it looks official with the company logo in the corner, and the tone sounds a lot like other emails you’ve received from the company. When you click the link, the page even looks like Amazon’s website. Even the checkout process is the same.
The message offers you an unbelievable discount on a laptop and provides a link to the buying page. You click the link to buy it, enter your credit card information, and complete your order.
However, you’ve just become a victim of a phishing attack. The product page was fake and disguised very convincingly like the real thing. Instead of placing your order, the website sent your payment details straight to a thief.
How Can you Recognize the Scam?
In the above case, there were three tell-tale signs.
- Once you log into your Amazon account to make the purchase, your payment method should be stored. Amazon rarely requires you to re-enter the number, unless you’re purchasing a gift card or shipping the item to someone else.
- If you look closely at the original email, it likely came from a spin-off domain with typos, extra extensions, and other things that demonstrate Amazon wasn’t the sender. For example, an email that’s anything other than @amazon.com.
- Another sign would be the lack of links on the actual product page. Amazon is loaded with products, pages, and other content. Even if the phishers tried to make it seem legitimate, there would be no way for them to replicate that.
Different Types of Phishing Attacks
With the rise of things like the Internet of Things (IoT), smartphones, and social media, the number of opportunities for phishing has grown considerably. Attacks can now affect more than just banking. PayPal, eBay, and Amazon accounts have all reported incidents of phishing attempts on unsuspecting customers.
Watch out for these common types of phishing attacks:
1. Deceptive Phishing
Deceptive phishing is the most well-known lure. This strategy involves impersonating a legitimate business’s website to steal data. It takes a phisher with strong knowledge in social engineering to pull this tactic off effectively.
2. Whaling
Also known as “CEO Fraud,” whaling occurs when a top executive at a company has his identity compromised. The phisher then orders employees to send funds to a separate account.
Whaling can also affect other high-profile individuals such as celebrities and politicians. Plus, given its focused nature, whaling can be difficult to detect since many departments never have contact with company executives.
3. Phishing Kits
Phishing kits are basically collections of software utilities you can download by mistake. Once installed, these tools can launch large phishing campaigns and send mass emails to spread the phishing attempts.
4. Spear Phishing
Some phishers can personalize the fraudulent messages they send you to make them more believable. These might contain your name, workplace, and phone number gathered through websites like LinkedIn. In fact, 95% of all attacks on enterprise networks are the result of spear phishing.
By its very nature, spear phishing is almost always used in whaling attempts and can involve impersonation of acquaintances and use of data from the victim’s social media sites, such as Twitter and Facebook.
5. Pharming
Pharming programs work through a bit of DNS trickery and automatically redirect your web browser to a malicious site even if you input the correct URL to a genuine site.
Pharming was the culprit in a 2005 hijack of New York Internet service provider Panix, in which the website was redirected to another unrelated website in Australia. No losses were recorded, but the outcome demonstrated how dangerous pharming can be.
To fight back against pharming, make sure you only enter login information and personal data on URLs beginning with “https,” which denotes a secured connection.
6. Login Interception
Pretending to be the login page for a major online service like Google Drive, for instance, is a common and effective tactic.
Utilizing two-factor authentication (using two different authentication factors to verify yourself, such as a password AND facial recognition software) can greatly reduce your chances of becoming a victim as every login will require a second form of authentication to legitimize the login.
Common Phishing Lures
There are many methods phishers have developed to lure you into submitting your personal information and data. Knowing what to look out for puts you in a better position to detect and overcome these types of attacks.
Some common phishing tactics include:
- An email claiming you’ve won a major prize or are at risk of losing access to your account. The message will prompt you to provide your login credentials or payment information to follow through with the prompt. Here’s how to avoid them.
- A phone call. There have been reports of fake Microsoft employees offering technical support for Windows machines. Once the victim gives the phisher access to his or her machine, the victim’s data is compromised. Here’s how to avoid them.
- A fake website. One of the most common types of phishing involves a fake website made to look like a real login page, such as the one to your Yahoo! email account. Phishers can gain a lot from accessing a victim’s email. Here’s how to avoid them.
You should also be on the lookout for:
- Threats of Deactivation. You receive an email from your bank threatening to shut down your account unless you verify your credit card information on their website immediately. In this example, the link they give you will lead to a fake site.
- The “Too Good To Be True” Scams. A common tactic is the “Nigerian prince” email scam. Written in a poor, almost comical style, the extravagant story promises great riches should the victim send payment information. As many of the stories go, the fake prince’s fortune has been locked behind a paywall. The scammer begs you to send money in order to restore access to this vast fortune, promising to pay you back many times over should you help. While it may seem ridiculous, the silliness of the message is intentional, as only the most gullible will fall for the trick.
- Fake FBI Arrests. A phisher wants you to act on impulse, and what gets you worried more than the threat of being arrested? In the United States, phishers might send fake emails, or even calls from the FBI or IRS, threatening arrests for random crimes like tax evasion or music piracy. Rest assured, the government will never send communication like this simply through an email and certainly won’t request funds with it. This type of lure tends to come bundled with ransomware as well, so avoid opening them at all costs.
- Fraudulent Tech Support. Fake 1-800 numbers are easier to obtain than you think. These types of phishers will offer to inspect your machine for malware, pretend to find it, and send in a software package to help you “fix” it. The irony is these scammers who offer to clean your computer will actually infect it with malware, keyloggers, and other phishing tools to extract your personal information. Remember, a random tech support agent from a large corporation will never call you unless you have contacted them first.
- Text Message Phishing. Even our cell phones aren’t safe anymore. SMS phishing solicits personal information through text messages in the same way an email or website phishing does, with the added concern of being unexpected. SMS Phishing can also result in vishing or voice phishing (telephone phishing).
- Hunting the Job Hunters. Phishers may sometimes post phony job offers on the Internet, primarily targeting teenagers who don’t know what they’re doing. Hired hands are employed to help in money laundering operations. While they sometimes do get paid like a real job, they’re also at risk of criminal charges as a result.
- Search Engine Viruses. Search engine viruses are essentially a Trojan with a strong standing in the search engine results. A virus might be advertised as the perfect solution to a technical problem you might be facing. SEO optimization plays a big role in ensuring the site shows up in your search. Once you download and install the Trojan, relieved you finally fixed your technical problems, the malicious code takes over and your problems only get worse.
- SWATting. While not a direct form of phishing, SWATting can be a dangerous consequence. SWATting occurs when the phisher steals the victim’s phone number and calls in a fake bomb threat. Emergency or not, having a SWAT team around your house is a stressful and dangerous experience, and in some cases, it can even be deadly, as SWAT teams are trained to treat every operation with maximum severity. Thankfully, modern law enforcement is now aware of SWATting attempts and usually knows how to handle them.
How to Protect Yourself from Phishing Attacks
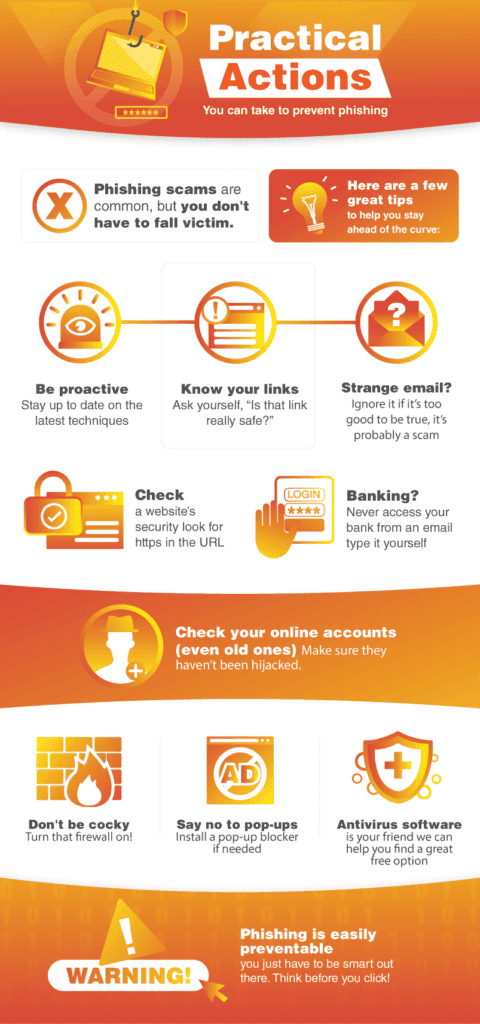
Phishing is clearly a serious issue every online user must address, but it still begs the question: “What can I do to protect myself and my business from a phishing attack?”
Educate yourself
Knowing that a problem exists is the first step to fighting back. Careless Internet surfing can leave you vulnerable to phishing attacks. If you’re a business owner, it’s also important to conduct training sessions with your employees to help them identify phishing scenarios, such as the ones mentioned above.
Among the lessons taught, get your workers to build good browsing habits, such as:
- Double-checking every link
- Never downloading unknown and untrusted attachments
- Always using different passwords for different accounts
- Changing passwords regularly
- Ignoring requests for file transfers, account transfers, or divulged passwords, even if they come from within the company
- Verifying all of the requests verbally before complying
Use Software to Defend your Devices Against Phishing
Your computer, when configured correctly, can protect itself. As a basic checklist, ensure that you have the following installed on every machine:
- Email spam filters, especially ones that look for suspicious links and unverified attachments
- Powerful antivirus solutions with security updates
- Web filters to block out malicious websites (usually these are built-in to antivirus programs)
- Anti-phishing toolbars and browser extensions that display the reputation of a website before you click the link
- A firewall (many antivirus programs come with a built-in firewall)
- Pop-up blockers
- An up-to-date web browser supporting all the modern security features
Preemptive Measures
As a business, you can take a few steps to prepare yourself in case a phishing attack breaches your servers. While ramping up your digital security with Microsoft’s Advanced Threat Analytics for your Windows-based machines is an option, you can also consider third-party cybersecurity insurance.
Decide on your needs based on how much you are willing to spend and how much you expect to save by protecting yourself.
Other Miscellaneous Tips
- Disable HTML emails if possible. Text-only emails cannot launch malware directly.
- Encrypt your company’s sensitive data and communications
- Check your bank account’s activity routinely for suspicious charges
The Best Security Software to Protect You from Phishing Attacks

Our experts have tried and tested all of the most popular antivirus programs available today. And while most of them offer adequate protection against most malware and viruses, not all of them offer good enough anti-spyware protection against phishing attacks.
That’s why we’d recommend investing in a powerful antivirus that comes with phishing protection, as well as making sure that these programs are updated regularly. See our top ten suggestions here.
How to Avoid Phishing Emails
Like many types of phishing attacks, you can’t prevent some malicious emails from entering your inbox. They’re common junk mail. You certainly can, however, learn to recognize what’s right from wrong and what to do when you’re at risk.
What they Look Like
Phishing emails might…
- Contain hyperlinks to suspicious websites with unrecognizable URLs.
- Contain attachments with ransomware, malware, and other viruses. Most file types can carry these viruses with the exception of the plain text file (.txt). Even Excel spreadsheets can contain malicious macros and code.
- Present a sense of urgency, such as a great deal on a product or a giveaway/lottery to call you to action.
- Refer to you as a “valued customer” without mentioning your name. Phishers, after all, don’t know who you are.
- Contain spelling and grammatical errors.
- Have a strange sent time, such as 4AM on a Sunday.
- Have an irrelevant or weird subject line.
- Be sent by addresses you aren’t familiar with, though keep in mind thieves can sometimes forge the identity of your coworkers to deliver a more potent phishing email. Check whether your acquaintances seem out of character in their emails.
How to Prevent them
- Spam filters are the most obvious solution. These usually come with most email clients and work by assessing the origin of the message and analyzing its content for spam-like characteristics. They aren’t 100% reliable and sometimes give false positives but are still worth using.
- Check the URL for any hyperlinks and determine whether or not the site it leads to is fraudulent.
- Never open attachments if you suspect a phishing email.
- Don’t click links in emails. At most, copy and paste the web address into your address bar.
- Simply be smart. Major organizations will never ask for your personal information directly through an email. They will more likely than not offer some form of verification in the email itself too, such as an account number.
- When in doubt, verify with the organization contacting you to ensure the communication is genuine.
How to Avoid Phishing Calls
Voice phishing, also known as “vishing,” is a phishing attack via telephones and Voice-over-IP services.
What They Sound Like
Vishing can take many forms, but some common examples are:
- Fake charities advertising a fake organization website.
- Fake calls from the government and IRS demanding action to prevent a major fine or arrest.
- Fake calls claiming to offer tech support and requesting access to your machine.
How to Prevent them
- Ask the caller if he or she knows your name. Vishers are not likely to.
- Know that your bank will never ask for sensitive information such as your Social Security Number, PIN, or password over the phone.
- Don’t be afraid to ask for verification that the call is not fraudulent. Legitimate businesses are happy to do so.
How to Avoid Phishing Websites
And finally, you have the usual fake websites masquerading as genuine online services. Most of the time, a phishing email might direct you to one of these.
What they Look Like
Malicious websites designed for phishing can be hard to identify sometimes, as attackers have become good at emulating the appearance and functionality of real sites. However, a key giveaway is the URL. Phishing sites may use a slightly different web address containing a small mistake.
PayPal is a commonly masked URL as the lowercase L could be replaced with an uppercase I. Look for these subtle clues before you engage with the site.
How to Prevent them
- Enable your web browser’s built-in protection settings. Many modern browsers will automatically block suspected phishing sites from opening.
- Report any phishing sites to the organization affected, such as your bank.
- If a website is asking for login credentials or sensitive information, ensure the site is legitimate.
- Contact the company beforehand to verify directly.
- Make sure the URL is both correct and contains the “https” heading denoting a secured connection.
- Use two-factor authentication whenever you can.
Famous Phishing Incidents from History
While phishing attempts are becoming more and more clever, it certainly isn’t a new cybercrime. Events like the hypothetical one above have occurred with disturbing regularity throughout the years, victimizing both individuals and entire corporations.
Here are some famous phishing attacks from history:
AOHell, the First Recorded Example
Back in early 1994, a malicious program called AOHell was developed by a Pennsylvania teenager and was intended to crack America Online (AOL) accounts.
Among other things, the program ran on top of the AOL client, stealing user’s passwords and using the program’s credit card generator to create fake accounts, which they would then use to impersonate AOL customer service. Regular users were asked to verify their accounts for security purposes, making this arguably the earliest form of phishing.
If you’re curious about the specifics of the AOHell scam, check out this paper by Koceilah Rekouche.
The Nordea Bank Incident
In 2007, Swedish bank Nordea lost over 7 million kronor when phishers managed to send fraudulent emails out to bank customers, luring them to install the “haxdoor” Trojan disguised as anti-spam software.
Dubbed the “biggest ever online bank heist” by digital security company McAfee, Nordea customers were hit with phishing emails containing Trojan viruses that installed a keylogger into the victims’ computers and directed them to a fake bank website where hackers intercepted login credentials.
While the exact blame can’t be reliably placed, it is worth noting that most customers failed to have a running antivirus installed on their machines.
Operation Phish Phry
2009 saw one of the FBI’s biggest cybersecurity busts ever after $1.5 million was stolen via bank frauds by various cyber thieves located in the United States and Egypt.
Former Director Robert Mueller noted that phishing attempts were a new part of the digital arms race, with cybercriminals always working to stay ahead of law enforcement by taking advantage of new developments in technology. He established the National Cyber Investigative Joint Task Force specifically designed for these kinds of attacks.
RSA
In 2011, the United States’s defense suppliers were breached when security firm RSA fell victim to spear phishing due to an Adobe Flash vulnerability.
Disguised as recruitment plans for that year, the email targeted mid-level employees with just one line of text: “I forward this file to you for review. Please open and view it.”. Only one employee had to open the email for phishers to gain backdoor access on the victim’s desktop. The phishers then managed to bypass the company’s SecurID two-factor authentication to steal company data.
Dyre Phishing Scam
In late 2014, malware produced by Russian hacker group Dyre resulted in the loss of millions of dollars. The phishers posed as tax consultants and convinced thousands of victims to download malicious executable files.
Dyre’s long list of victims included paint and materials company Sherwin-Williams, engine parts manufacturer Miba, airliners RyanAir, and several other companies throughout the US, the UK, and Australia.
When the victim failed to enter their credentials into the fake phishing site, the hackers called the victim through Skype pretending to be law enforcement officers and bank employees to encourage the transfer.
While the final arrests were made in late 2015, the legacy of the cyberattack lives on. A new phishing malware named TrickBot was created shortly after, using the same elements from Dyre to target similar financial institutions.
The Sony Pictures Leak
2014 also saw a huge data leak from Sony. Over 100 Terabytes containing confidential company activities was breached, resulting in well over $100 million lost. The phishers pretended to be colleagues of the top-level employees who opened the malicious attachments in the phishing emails.
Specifically, a fake Apple ID verification email was used in the attack. Through a combination of LinkedIn data and Apple ID logins, the phishers managed to find passwords that matched the ones used for the Sony network – a great example of why using different passwords for different online accounts is so important.
Facebook and Google
This is a huge one. Two of the world’s largest tech giants, Facebook and Google, lost $100 million in this single email scam from Lithuania. While an arrest was made, the story shows that even the most advanced tech entities are susceptible to phishing attacks.
2018 World Cup
The Federal Trade Commission released a statement regarding phishing attempts during the 2018 World Cup in Russia. The scam claimed the victim won tickets to the World Cup through a lottery and prompted them to enter their personal information to claim the prize.
At the same time, a handful of rental scams were reported as well. Cybercriminals stole the email addresses of genuine landlords in Russia and offered ridiculously low prices for their properties during the sporting event. Once a “lucky buyer” accepted the offer, his or her credit card information was stolen.
Let’s Summarize:
- Phishing is a cybercrime when someone pretending to be a trustworthy entity solicits sensitive information from an unsuspecting user.
- Phishing is a common problem that has cost millions of dollars in damages to companies and individuals.
- Installing the right web filters, spam filters, and antivirus software can help make your machine phishing-proof.
- Good browsing habits and general education about the phishing threat are your best line of defense, especially for businesses.
- Make sure you and your employees understand how to combat phishing by email, phone, and websites.
- Phishing emails may contain malicious attachments and links to fraudulent websites.
- Phishing phone calls may direct you to provide your information to seal a deal, avoid criminal charges, or provide fake support.
- Phishing websites may masquerade as a real login or buying page and steal your credentials or credit card information.
There are many phishing scams out there, and as we’ve learned, they target more than just the average Internet user. But they aren’t a death threat. There are plenty of easy steps to take to lower your chances of losing your data to phishers.
Remember, phishing attacks are evolving too, so it’s important to have an up-to-date antivirus with phishing protection and ensure ongoing security awareness training for all employees in your company to stay informed of the latest best practices.
A little awareness now can save you a lifetime of battling debt collection agencies and cases of identity theft. Let’s rather be safe than sorry.