
Updated on: April 26, 2024
Short on time? Here’s the best antivirus for 2024:
- 🥇 Norton: Excellent virus and malware protection, with tons of extra features like anti-phishing, a VPN, a password manager, parental controls, live dark web monitoring, cloud backup, and a lot more.
There are hundreds of antiviruses out there — and they all claim to offer the best protection at the best price. But I tested the top antivirus software on the market and only a few of them are strong enough, secure enough, and effective enough to be considered one of the best antiviruses of 2024.
Most antivirus programs nowadays include more than just a virus scanner — they also come with features that add additional protection, like a network firewall, phishing protection, a virtual private network (VPN), a password manager, parental controls, as well as dedicated protections for mobile devices.
But a lot of antiviruses don’t exactly work as advertised — they have poor malware detection rates, they don’t consistently block malicious sites, and their extra features are badly designed and virtually useless (despite charging you an extra fee).
I spent weeks testing the top antiviruses on the market — I ranked them on security, functionality, speed, and price. Norton came out on top, but I found 10 other products that are also excellent. Read on to find out more about each of them and decide which is best for you.
RISK-FREE FOR 60 DAYS — TRY NORTON NOW
Quick summary of the best antivirus software for 2024:
- 1.🥇 Norton — Best overall antivirus in 2024 with excellent malware protection for all kinds of devices.
- 2.🥈 Bitdefender — Best for lightweight malware scanning (with heaps of additional features and tools).
- 3.🥉 TotalAV — Best for ease of use (with beginner-friendly apps and tools for all major devices).
- 4. McAfee — Best for web protection (with parental controls and a great family plan).
- 5. Intego — Best for protecting your Mac + comes with great optimization toolset.
- Numbers 6-10 of 2024‘s top antiviruses.
🥇1. Norton 360 — Best Antivirus for Windows, Android & iOS
Norton 360 offers unbeatable virus and malware protection. It’s a well-built and well-maintained internet security suite that fully ensures all information stays secure, private, and protected — and it works well across all operating systems. It’s the best choice for home users looking for a complete, intuitive antivirus with some of the best cybersecurity protections out there, all for a low-cost yearly subscription.
Norton’s antivirus software uses a unique scanning engine powered by heuristic analysis and machine learning, making it capable of scanning, finding, and removing all of the newest and most advanced types of malware. It scored a 100% protection rating during all of my independent tests, and it consistently scored higher on detection and threat prevention than built-in antiviruses (like Windows Defender).
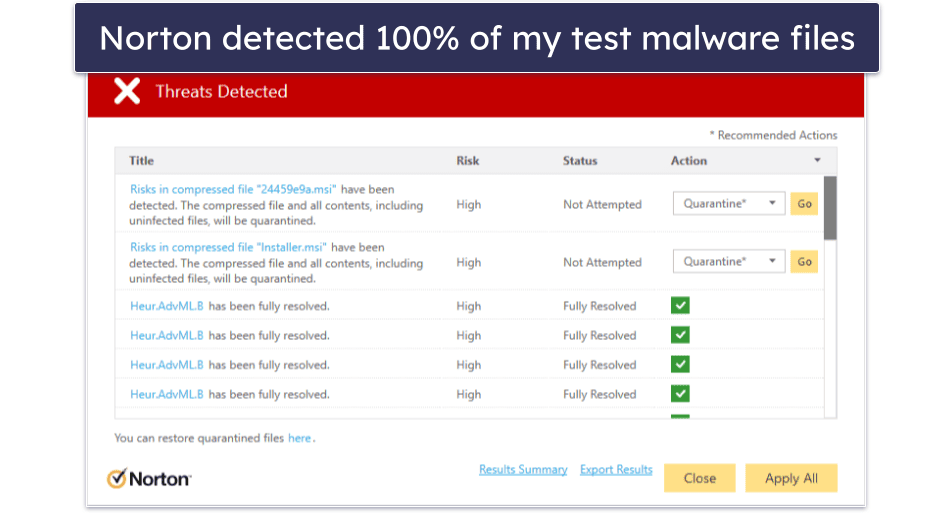
Norton 360 comes with a wide range of additional features — and they’re all easy to use and work just as promised. The features include:
- Secure firewall.
- Password manager.
- Webcam protection.
- VPN (with unlimited data).
- Dark web monitoring.
- Cloud storage (250 GB on the 360 with LifeLock Select plan).
- Secure browser.
- Ransomware protection.
- And a lot more…
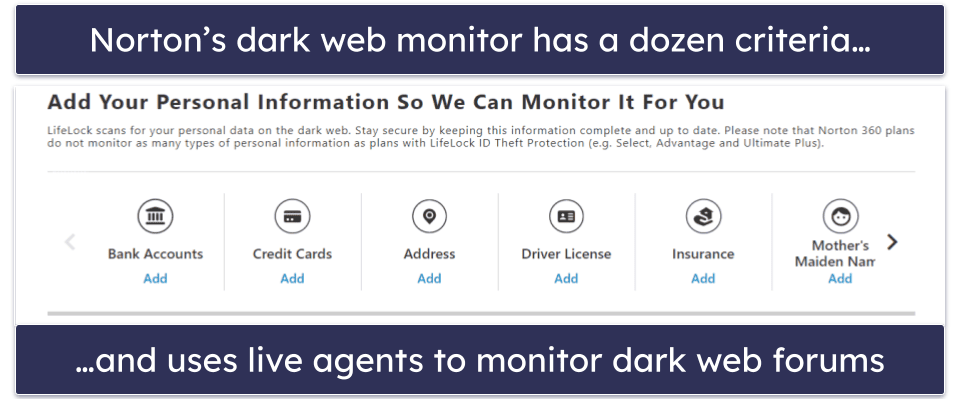
My favorite extra is dark web monitoring (it’s by far the best dark web monitoring tool I’ve ever tested). It constantly scans the dark web for a wide range of personal information, including credit card details, insurance documentation, home addresses, phone numbers, gamer tags, and more, and it immediately alerts you if it detects any stolen data.
Norton also includes a decent password manager — an important tool for maintaining good online security. It generates strong passwords and stores them, so you never have to remember them. Unfortunately, it lacks password sharing and a built-in TOTP authenticator like some standalone competitors include, but it does the basics well.
Norton is also a great choice if you reside in the US and are in the market for identity theft protection. Norton’s LifeLock products offer various levels of protection and reimbursement, including up to $3M coverage in stolen funds, personal costs, and lawyer/expert expenses. Among other features, it includes alerts for “buy now, pay later” charges made on your account and prevents loans from being taken out in your name. These plans can be purchased separately or bundled with the antivirus.
Norton’s VPN is one of my favorite antivirus-bundled VPNs in 2024, thanks to its unlimited browsing data across all 360 plans. It offers robust security features, including 256-bit AES encryption, a kill switch, and a no-logs policy, alongside additional perks like Wi-Fi security, split-tunneling, an ad blocker, and Tor compatibility. It has servers across 30+ countries, good connection speeds, and it supports Netflix, Max, Amazon Prime, and more. It’s available as part of Norton’s Standard, Deluxe, and LifeLock plans or as a standalone purchase — it’s a good option if you’re seeking encrypted web access with extensive device coverage.
I also like the webcam protection feature, which stops unauthorized access to your webcam. It worked pretty well in my tests — making it a reliable choice for individuals worried about cybercriminals spying on them.
Norton provides excellent value across all of its packages. Priced at $29.99 / year*, its entry-level AntiVirus Plus plan doesn’t come with a lot of features, but it still has real-time malware protection, a firewall, a password manager, and 2 GB secure cloud storage. Norton 360 Standard is also a pretty good deal — it adds unlimited VPN access and dark web monitoring and covers 3 devices for $39.99 / year*.
Norton 360 Deluxe is the best-value package for most users — for $49.99 / year*, you get more licenses (up to 5), more storage space (up to 50 GB), and access to some of the best parental controls on the market. Starting at $99.99 / year*, Norton 360 with LifeLock Select also adds identity theft protection and credit monitoring via Norton’s sister company, LifeLock — but these advanced plans are only available for US customers.
Bottom Line:
Norton 360 provides the best antivirus protection in 2024. It offers one of the strongest cybersecurity packages around — complete protection from all malicious threats alongside a ton of excellent extra features, like a VPN (with unlimited data), a password manager, secure cloud storage, parental controls, and a lot more. You can try Norton risk-free with the company’s 60-day money-back guarantee.
Read the full Norton review here >
🥈2. Bitdefender Total Security — Best for Lightweight Scanning + Tons of Additional Features
Bitdefender has an extremely advanced antivirus engine — it uses a massive malware database together with machine learning and artificial intelligence to detect and protect against malware more effectively than almost any other competitor on the market.
Bitdefender found and removed every malicious threat from my system when I tested it. And because its engine is cloud-based, all of the malware scans take place on Bitdefender’s cloud server, offloading the strain on your device. Bitdefender caused virtually zero system impact to both my Windows and Mac laptops, even during intensive, full-disk scans.
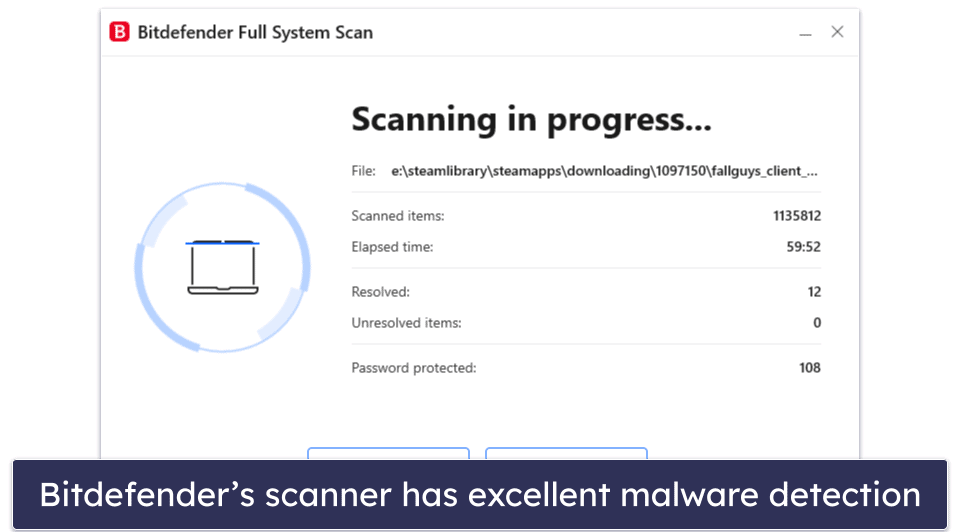
But Bitdefender isn’t just an anti-malware scanner — it’s one of the most comprehensive security suites available, providing some of the best protection for both computers and mobiles, with features like:
- Web protection.
- System optimizer
- VPN (200 MB/daily on most plans).
- Parental controls.
- Password manager.
- Webcam protection.
- Ransomware protection.
- And a lot more…
Bitdefender’s web protection is excellent — the anti-phishing protection blocked the vast majority of phishing sites in my testing, and I’m a big fan of Safepay, which is a secure, encrypted browser window for online banking and shopping. I particularly love Bitdefender’s multi-layer ransomware protection, which adds a data-protection layer over your important files so that they can’t be encrypted during a ransomware attack.
Bitdefender’s VPN is also one of the best on the market, providing lightning-fast access to encrypted servers around the globe — unfortunately, unlike Norton’s VPN, Bitdefender’s VPN limits your daily data usage on all but the most expensive plans.
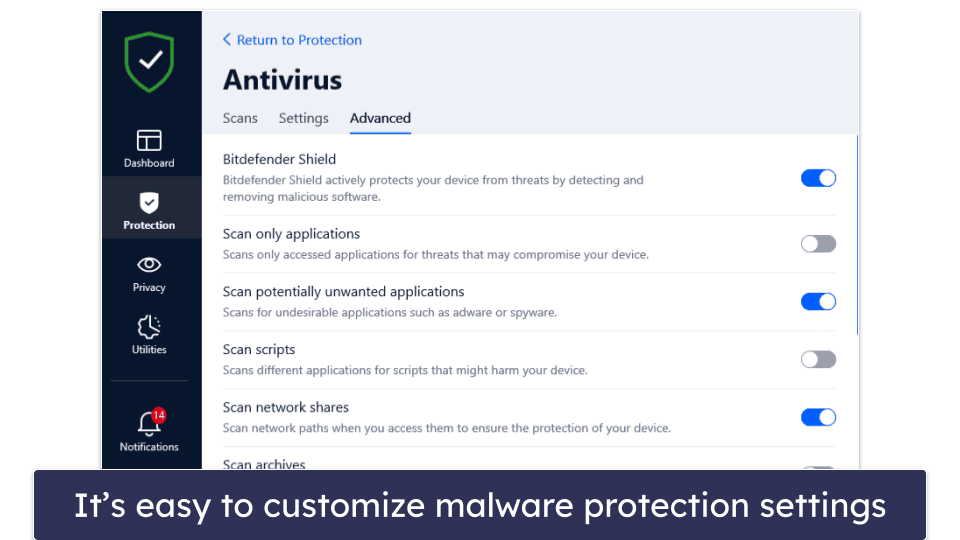
Similar to Norton, Bitdefender includes advanced settings for users who know how to customize their antivirus protection. You can set custom scan settings for specific areas of your computer, like scripts, network shares, boot sectors, and even new/modified files. Bitdefender’s advanced settings help further its reputation as one of the most powerful and customizable malware scanning engines out there.
Bitdefender has several low-cost packages available. Bitdefender Antivirus Plus, which is priced at $29.99 / year, has many of Bitdefender’s premium features (except webcam protection, parental controls, and a device optimizer), but it’s only available for Windows. Bitdefender Internet Security adds on parental controls, a firewall, and coverage for up to 3 Windows computers for $42.49 / year.
My favorite plan is Bitdefender Total Security, which includes 5 licenses for Windows, macOS, Android, and iOS for $49.99 / year. There’s also Bitdefender Premium Security, which includes all of Bitdefender’s features, plus the VPN with no limitations — at $79.99 / year, it’s pricier than some competitors, but considering the VPN is as good as the top standalone VPNs, I still think it’s worth it.
Bottom Line:
Bitdefender offers cloud-based scanning and heaps of cybersecurity tools for a cheaper price than most competitors. I recommend Bitdefender if you’re looking for a comprehensive cloud-based cybersecurity suite with extras like a VPN, parental controls, and a password manager. And you can try out Bitdefender risk-free with a 30-day money-back guarantee.
Read the full Bitdefender review here >
🥉3. TotalAV — Best for Ease of Use (Super Beginner-Friendly)
TotalAV has an excellent antivirus scanner and a couple of really good extras, all inside a very intuitive dashboard — making it a particularly great choice for beginner users who don’t want to deal with complicated menus and settings. However, TotalAV also includes many customization options that advanced users will appreciate.
TotalAV’s antivirus scanner is fast and reliable, with near-perfect malware detection rates. The scanner caught 99% of all of my test malware, from viruses and trojans to ransomware, missing only a couple of tricky files (which Norton and Bitdefender managed to catch).
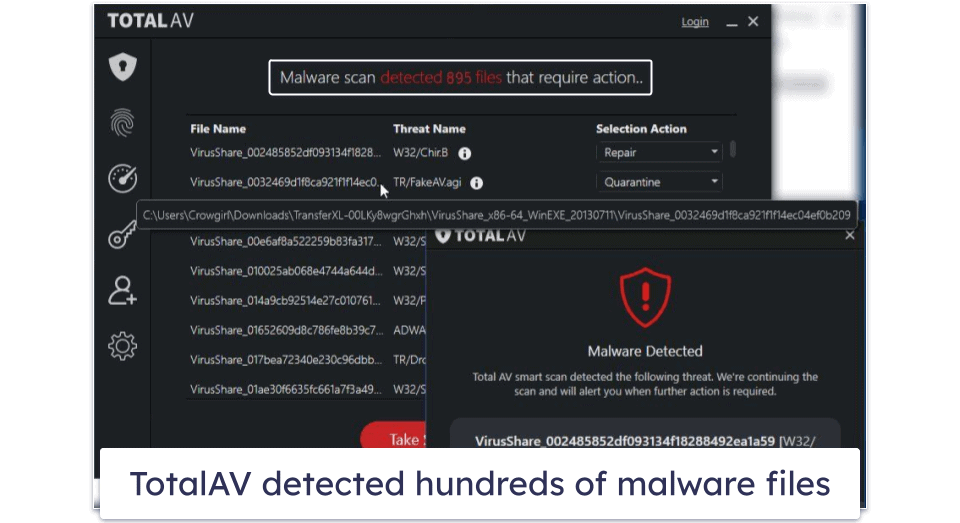
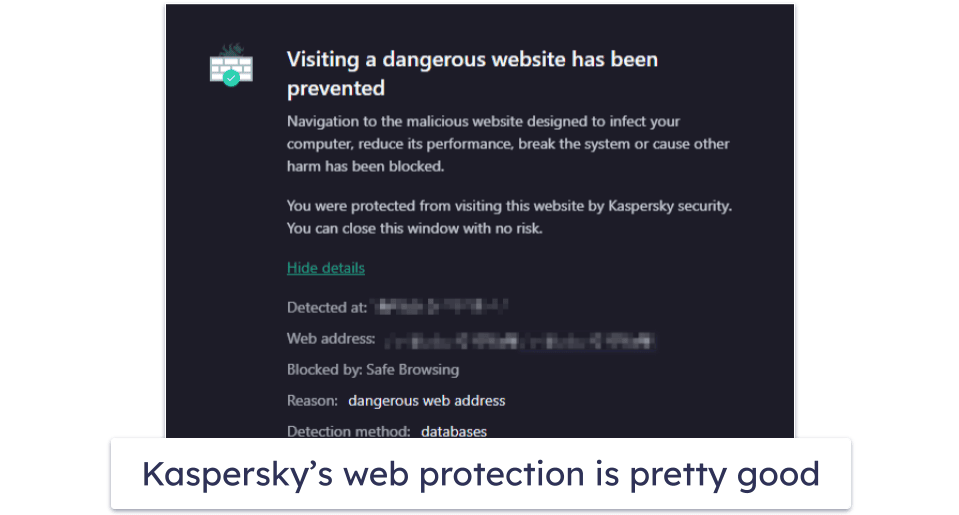
TotalAV’s WebShield stops you from visiting dangerous websites. It does this by comparing websites you visit with a blacklist of unsafe websites and blocking any matches. During my tests, it outperformed Chrome and Firefox, blocking dangerous websites that both of them missed.
Furthermore, TotalAV’s Smart Scan simplifies routine maintenance tasks by compacting them into 1 scan. This includes an antivirus scan, tracking cookie scan, and disk cleanup. I appreciate the amount of time I saved while running this scan.
You also get a full range of extra internet security features. I particularly like TotalAV’s performance optimizer (which you can run separately from the Smart Scan). During my tests, it cleaned up more space on my computer than most other competitors. I also like TotalAV’s VPN — it’s secure, works with popular streaming sites, and maintains pretty fast speeds across all servers (which is why it ranks as one of the best antivirus-bundled VPNs on the market).
The password manager is pretty good, too. Total Password provides a secure way to store all of your passwords and other bits of sensitive information in an encrypted space. You get all of the standard features, like auto-saving and auto-filling, a customizable password generator, cross-device synchronization, and more. It performed really well in my tests, with my only complaint being that it lacks password sharing. That said, it does include some pretty unique features like Secure Me — a tool that lets you remotely log out of accounts on all devices.
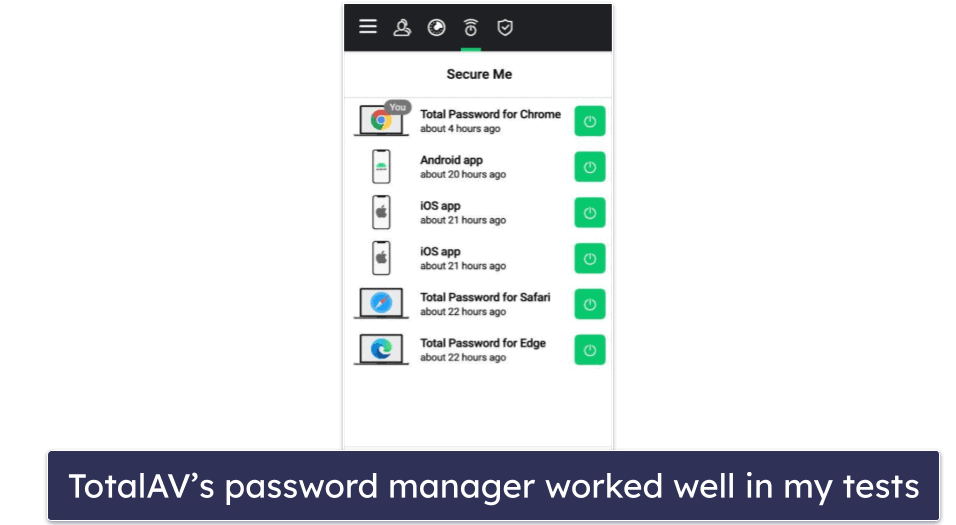
My favorite plan is TotalAV Total Security, which covers up to 6 devices and costs $49.00 / year. It includes a VPN, premium password manager, and excellent ad blocker alongside all the other features mentioned above. If you’re on a budget, TotalAV Antivirus Pro is a good entry-level package for users looking to protect up to 3 devices, and it costs $19.00 / year. All plans come with a 30-day money-back guarantee.
Bottom Line:
TotalAV has a powerful antivirus engine and a good range of features inside a user-friendly dashboard — I recommend TotalAV for first-time users just needing something safe, secure, and easy to use. TotalAV’s packages all have a wide range of features, and they’re all designed for maximum ease of use. Plus, all TotalAV purchases have a 30-day money-back guarantee.
Read the full TotalAV review here >
4. McAfee Total Protection — Best for Online Security (+ Great for Families)
McAfee Total Protection has a great range of internet security features — malware protection, anti-phishing protection, a password manager, a VPN, and identity theft monitoring and coverage. And all of its features are intuitive, easy to use, and work just as promised.
Its excellent virus protection abilities alone make McAfee a great choice — scoring a perfect 100% detection rate against all of the malware samples during my series of tests. McAfee detected, blocked, and removed both simple and advanced threats, including viruses, trojans, spyware, keyloggers, and rootkits.
Its anti-phishing protection is also excellent, preventing me from accessing known phishing sites and other dangerous web pages. It identified the vast majority of risky sites, outperforming both built-in protections from browsers like Chrome and Firefox and web protection from most competing antiviruses.
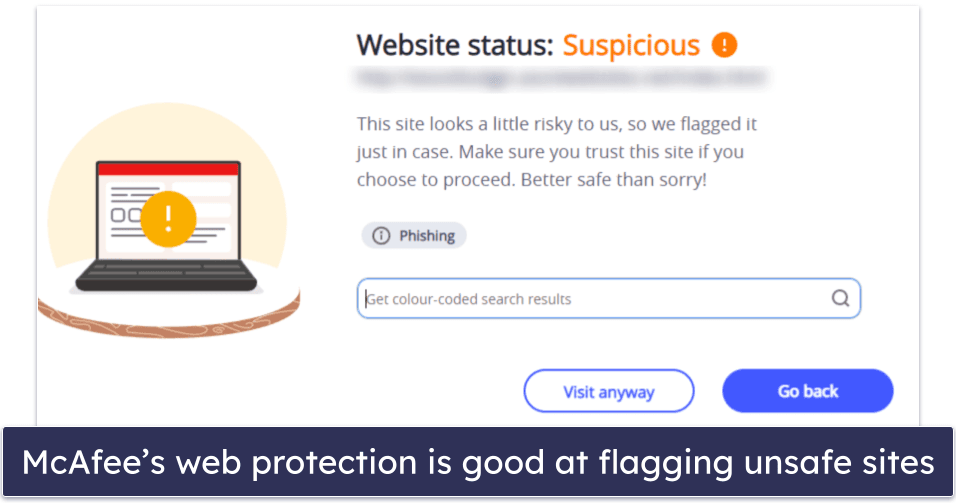
Additionally, McAfee’s Scam Protection protects you from scams by warning you about dangerous links in emails, texts, social media, or web browsers. I liked how it quickly flagged malicious links, making it easy to avoid dangerous sites.
The Wi-Fi scan feature in the mobile app is great, too. It checks the Wi-Fi network you’re connected to and lets you know if the encryption is good enough to keep your info safe. I found it useful when on the move — it alerted me to vulnerabilities on open networks (like in coffee shops) and helped me decide whether to stay connected or find a safer network.
McAfee’s parental controls are also some of the best on the market — in addition to blocking inappropriate and unwanted content and apps, they also come with advanced location tracking, which allows you to track your child’s device with almost perfect accuracy (this feature works much better than Google or Apple’s tools for locating devices).
However, McAfee did slow down my computer a bit during full system scans (unlike Norton and Bitdefender). While I was able to browse the internet, use Microsoft Office, and watch videos on YouTube (there was some buffering), I couldn’t play CPU-intensive games as my screen kept freezing during gameplay.
McAfee’s plans, which start at only $39.99 / year, offer excellent value. The Plus plan ($39.99 / year) provides coverage for up to 5 devices, and the Premium family package ($59.99 / year) adds parental controls and coverage for an unlimited number of devices. There’s also the Advanced ($79.99 / year) and Ultimate ($179.99 / year) plans, which add identity theft coverage of up to $1 million and other protections. Ultimate is distinguished by more extensive credit monitoring and the addition of ransomware insurance.
Bottom Line:
McAfee Total Protection offers a great range of internet security protection for all computers and mobiles. Its anti-phishing and Wi-Fi protections are exceptionally good, blocking all risky sites and offering centralized security control from the McAfee mobile app, and its parental controls are some of the best on the market. This makes McAfee Total Protection particularly great for families looking to keep a highly secure Wi-Fi network and improve their children’s safety both online and offline. All Total Protection packages include a commitment-free 30-day money-back guarantee.
Read the full McAfee review here >
5. Intego — Best for Comprehensive Mac Protection
Intego is the best macOS antivirus out there. Most antivirus brands only focus on protecting Windows PCs — even competitors like Norton offer far fewer features for their macOS programs than they do for their Windows versions. But all of Intego’s Mac antivirus packages were exclusively designed to provide high-quality internet security and optimization tools for macOS. It greatly enhances Apple’s built-in safety features with things like:
- Real-time malware protection.
- Mac optimization and cleaning tools.
- Advanced Mac backup options.
- Network security options.
- Parental controls.
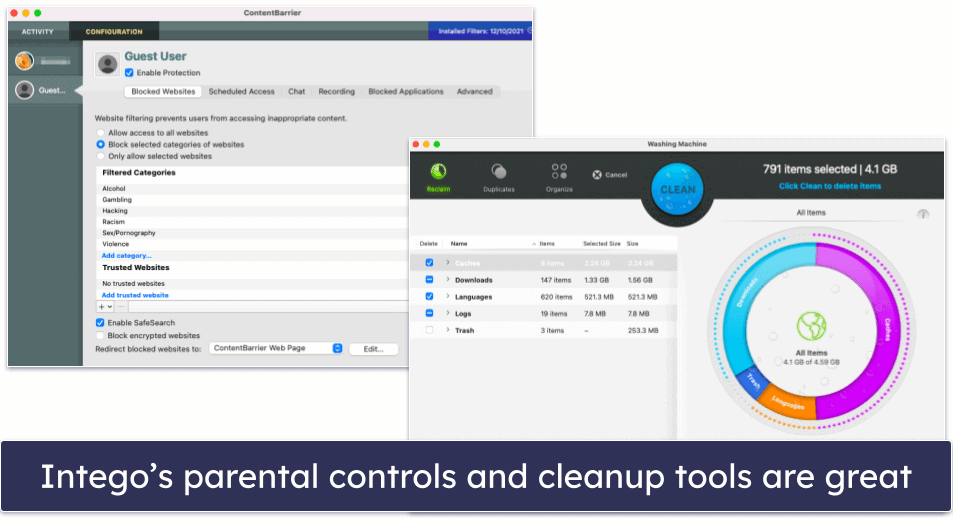
Intego’s antivirus engine scored a perfect detection rate against all of my test malware (both macOS and PC malware). And its scans are fast — scanning over 800,000 files in under 2 hours. I also really like that subsequent scans take only a few minutes, thanks to Intego’s file caching system that ignores already-scanned files (Norton uses the same technology to skip over previously scanned files).
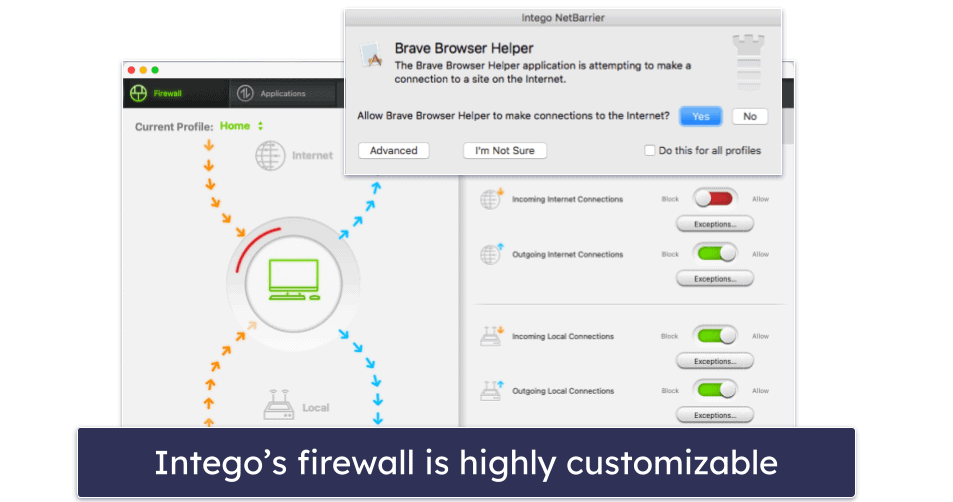
I’m also a huge fan of Intego’s customizable smart firewall — it monitors both incoming and outgoing network connections and alerts you to programs trying to connect to the internet, which prevents programs from sending data from your Mac without you knowing (perfect for stopping hidden spyware attempting to send sensitive information to hackers). The firewall also adjusts its settings automatically depending on your environment — if you’re at home, work, or using a public Wi-Fi network — ensuring you have the most appropriate settings switched on.
Intego has a lot of pretty cool additional features — I particularly like how you can connect an external drive or an iOS device to your Mac and run an antivirus scan of it with Intego’s virus scanner. Because Intego doesn’t offer internet security protection for mobile, this saves you from needing to get multiple antivirus packages to protect your iOS devices — but if you want to do more than run antivirus scans on iOS, you’ll need to get a separate iOS antivirus app.
Intego’s Mac Premium Bundle X9 plan is excellent — it comes with all of Intego’s best features, including disk optimization tools and parental controls. There’s also the Mac Internet Security X9 plan, but it only has real-time malware protection and a firewall. Starting at $19.99 / year, Intego is a bit more expensive than the competitors, but then again, most competitors offer very basic programs for Mac users (typically only malware scanners).
Intego also has a Windows product, Antivirus for Windows, that offers a level of malware protection on par with the best antiviruses on this list. It detected 100% of the malware samples I used to test it. But even though it’s effective, Intego’s antivirus for Windows isn’t a full suite like Intego’s Mac products. If you need a Windows antivirus, most of the other ones on this list are better choices.
Bottom Line:
Intego is the best antivirus for macOS in 2024 — it offers excellent protection against Mac-based malware, it greatly enhances and improves upon Apple’s already built-in security and device optimization tools, and it comes at a great price. And there’s a 30-day no-risk money-back guarantee, so you’ll be able to see if it offers the best protection for you.
Read the full Intego review here >
6. Panda Dome — Best for Flexible Pricing
Panda offers an advanced virus scanner and easy-to-use interface, and it has 4 different pricing plans to choose from — I love that Panda provides its excellent security solution to everyone, regardless of budget. I’m also happy that Panda’s malware scanner performed well during testing (95% malware detection rate and 100% ransomware detection rate), and I liked most of the additional features too.
However, I was disappointed with Panda’s VPN — it didn’t perform well in speed tests, and the unlimited-data VPN is only available on the most expensive plan. If you’re looking for a VPN included in an antivirus package, I’d recommend Norton or TotalAV.
On the other hand, I really like the Rescue Kit, which is a bootable version of Panda that can be operated from a thumb drive (in case your computer gets heavily infected by malware).
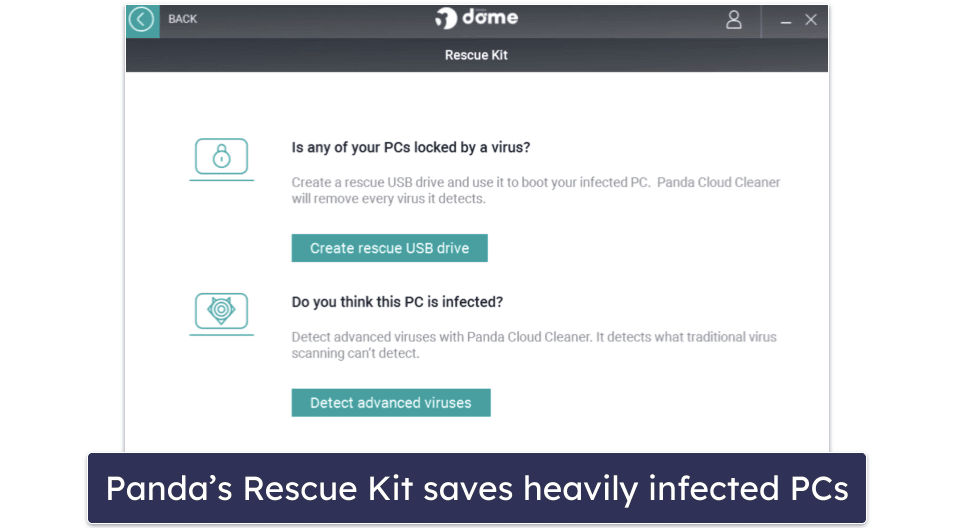
There are a few different Panda plans to choose from, including a fairly limited free plan. Panda Free includes real-time virus protection for Windows and an app scanner for Android, plus a Rescue Kit and a VPN (limited to 1 server and 150 MB per day).
Essential, the most basic paid plan ($23.99 / year), adds a firewall and Wi-Fi protection. The Advanced plan goes for $28.49 / year and adds ransomware protection, while Complete ($42.99 / year) gets you a password manager and various optimization tools. Panda Dome Premium adds an unlimited-data VPN and grants you access to 24/7 customer support for $66.99 / year. All plans come with a 30-day money-back guarantee and let you choose how many devices you want to protect.
Bottom Line:
Panda has an option for every user, whether they want a simple free malware scanner with real-time protection or a full-featured internet security suite. Panda comes with lots of extras, including advanced ransomware protection, a Rescue Kit for saving malware-infected PCs, a password manager, parental controls, and a file encrypter and shredder. And all of Panda’s premium plans are backed by a 30-day money-back guarantee.
Read the full Panda review here >
7. Kaspersky Premium — Best for Online Shopping + Banking
Kaspersky Internet Security has excellent antivirus protection, plus some impressive bonus features like dangerous site protection that will help keep you safe online. Its antivirus engine consistently delivers some of the best results in the industry against all types of malware — the program was 100% effective in all of my anti-malware testing.
Kaspersky also includes a good variety of cybersecurity features, such as:
- Anti-phishing protection.
- Safe Money secure browser.
- VPN (unlimited data).
- Password manager.
- Smart Home Monitor.
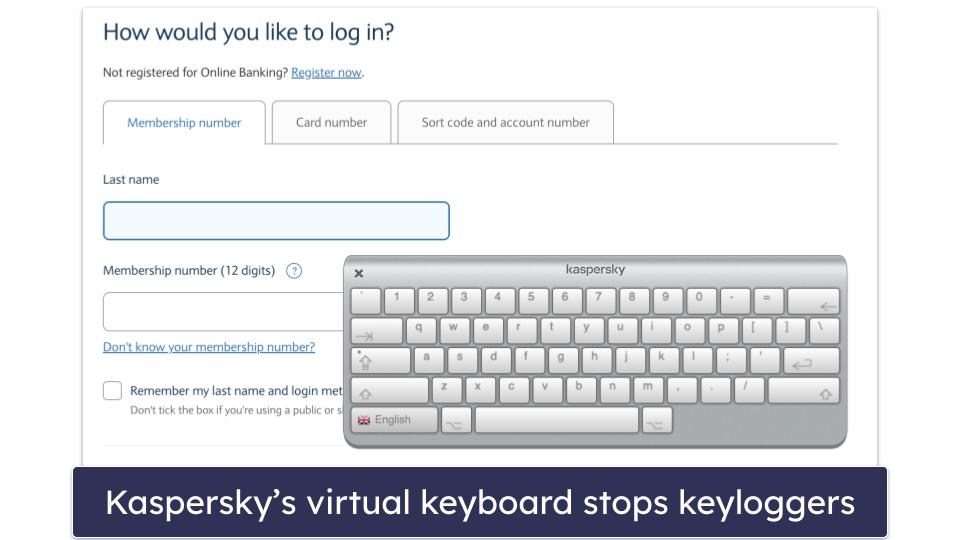
I really like Kaspersky’s Safe Money feature — the program detects when you’re about to make a payment online or access a banking website, offering to launch a safe, sandboxed browser window that’s impenetrable to malware and spyware. While I’m a fan of Safe Money, I slightly prefer Bitdefender’s secure browser, Safepay, which loads much faster than Kaspersky’s. Kaspersky also lets you use a virtual keyboard when handling online payments to avoid keyloggers.
On the other hand, the vulnerability scanner was a bit of a letdown. The scan for vulnerabilities took ages and failed to detect any vulnerabilities. I didn’t expect this, since Kaspersky’s built-in app updater had already identified outdated applications on my system.
Kaspersky has 1 free and 3 paid plans. The free plan gives you basic protection on a single Windows device. To protect your Android, MacOS, and iOS devices, you’ll need to upgrade to a paid plan. While Kaspersky Standard and Plus are both good options that come with most of the features mentioned in this review, Kaspersky Premium is the best-value plan, providing malware scanning, web protection, the Safe Money secure browser, an unlimited-data VPN, a password manager with unlimited password storage, home Wi-Fi monitoring so you can keep track of who connects to your network, and 1 free year of Kaspersky parental controls for up to 1 user. At only $74.99 / year, this is a good deal — and there are also options to cover 5, 10, and even 20 users depending on your location.
Bottom Line:
Kaspersky offers a well-designed antivirus package with a good anti-malware scanner. In addition, you get useful extras like a secure browser for online finances, a VPN, a password manager, and 1 free year of parental controls. All of Kaspersky’s plans have a 30-day money-back guarantee.
Read the full Kaspersky review here >
8. Avira Prime — Best for System Optimization
Avira has one of the strongest and most robust antivirus engines around — it consistently earns high scores during independent testing (and scored a 100% detection rate during all of my tests), and it’s so good that Avira’s anti-malware technology has been licensed out to several competitors, including TotalAV.
Avira Prime also comes with a lot of really good additional features, such as:
- Privacy optimization.
- System optimization.
- VPN.
- Password manager.
- Premium apps for Android and iOS.
Avira’s system optimization tools are some of the best on the market. While many antivirus products include tune-up tools designed to help your device run smoothly and free up hard drive space, Avira comes with the most advanced tune-up and clean-up tools bundled with an antivirus, including:
- Startup optimizer. Saved a full 2 minutes from my PC’s start time!
- Game booster. Automatically allocates system resources and stops background processes to improve system performance.
- Junk file cleaner. Removes duplicates, unused files, and some cached files.
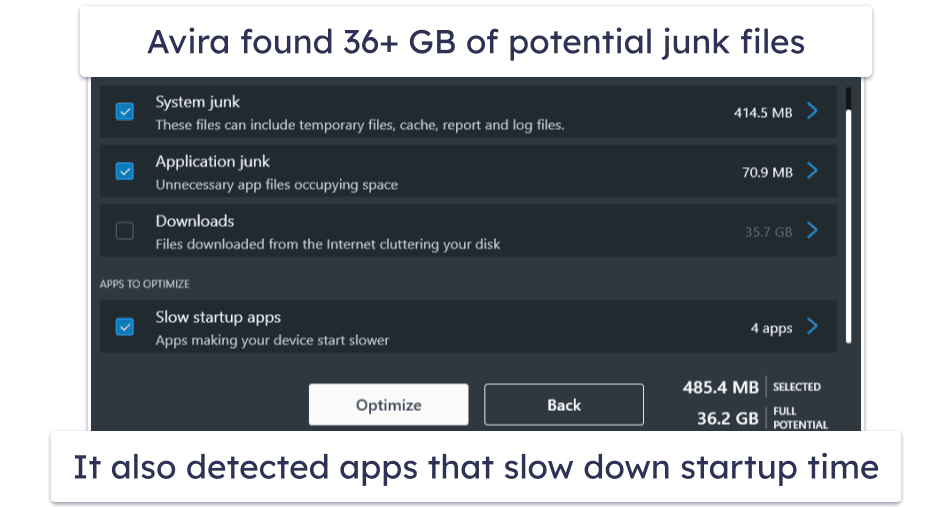
Avira Prime is a particularly good antivirus if you have an old or slow PC that’s often low on hard disk space. Avira’s system optimization tools had my old Windows 7 computer running like new — in fact, it almost seemed faster than my new Windows 10 PC! And since Avira’s antivirus engine operates entirely in the cloud, it won’t slow down your devices like many other competitors that download bulky software packages to your system.
At $59.99 / year, Avira Prime is a good value, but it’s pricier than some top-rated antivirus packages. Avira does have cheaper plans, including Internet Security ($34.99 / year), but Prime is the only package that includes advanced system optimization, the unlimited-data VPN, and mobile apps.
Avira’s free version is one of the better free antiviruses software on the market — if you don’t want to spend any money right now, Avira Free can help keep your device protected with real-time protection, ransomware protection, and even a free version of Avira’s VPN.
Bottom Line:
Avira is the most lightweight security suite on my list, with a cloud-based scanner and excellent system optimization tools. It also has a VPN, password manager, and coverage for up to 5 devices across all operating systems. You can try out Avira risk-free with a 60-day money-back guarantee.
Read the full Avira review here >
9. Trend Micro — Best for Secure Web Browsing
Trend Micro has a decent anti-malware engine, as well as an excellent web browser extension that monitors security risks, blocks online scams, and checks websites for unsafe content. The antivirus scanner scored pretty well in my testing, catching the majority of viruses, trojans, ransomware, and spyware on my system, though it didn’t score as well as top competitors like Norton and Bitdefender. Trend Micro also offers several scan customization settings, allowing users to adjust the malware protections.

Trend Micro detected more phishing websites than Chrome, Firefox, or Safari when I tested it. In addition, it detected scam links, unsafe content, malicious code, and even misinformation, and it also blocked ads and scanned my browsing history for any dangerous sites I may have visited accidentally.
Trend Micro also includes a password manager, secured with 256-bit AES encryption. It offers basic features like unlimited password storage, password generation, basic autofill, and two-factor authentication. However, compared to top competitors like 1Password and Dashlane, it’s less intuitive and feature-rich. That said, it remains a solid basic choice for password management.
Starting at $14.95 / year, Trend Micro offers several plans to choose from. Trend Micro Antivirus + Security protects 1 Windows device with malware protection, advanced ransomware protection, and a secure browser for online finances. Trend Micro Internet Security protects up to 3 devices (PC only) and adds device optimization tools, social networking protection, and parental controls. Trend Micro Maximum Security protects up to 5 devices (including Windows, Android, Mac, iOS, and Chromebook) and adds a password manager. The most comprehensive plan, Premium Security Suite, costs $54.95 / year, covers up to 10 devices, and adds various identity theft protections and a fully-featured VPN.
Bottom Line:
Trend Micro offers a strong set of malware and internet security features for Windows, Mac, Android, iOS, and Chromebook users. It’s particularly good at web protection, and its browser extension will help you avoid malicious websites, scam links, and suspicious content. All Trend Micro plans are backed by a 30-day money-back guarantee.
Read the full Trend Micro review here >
10. Malwarebytes — Best for Basic Protection
Malwarebytes is a simplistic, easy-to-use antivirus that offers good virus protection for all operating systems and devices. During my tests, Malwarebytes’s advanced malware scanner detected around 95% of my test malware, which is pretty good (but not as good as top competitors like Norton).
Malwarebytes also offers a VPN with unlimited data, servers in 40+ countries, and decent speeds. However, Malwarebytes’s VPN isn’t a good choice for streaming or torrenting (if you’re looking for a good VPN to securely watch streaming sites and torrent files, I recommend ExpressVPN).
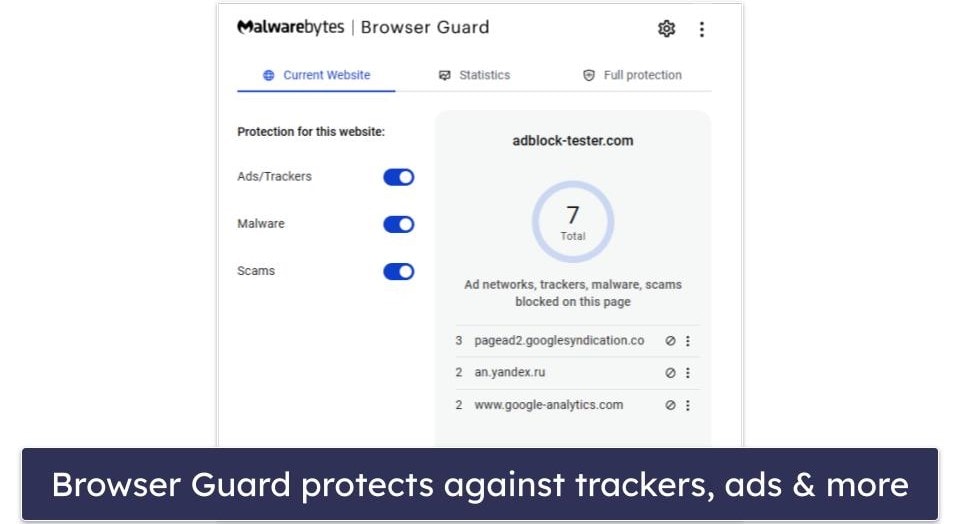
That said, I’m a big fan of Malwarebytes’s web protection, which successfully identified and blocked most of the phishing sites I tried visiting during testing, as well as ads, trackers, and other potential scams. Unfortunately, Browser Guard, which is supposed to enhance browser speed by obstructing ads and unwanted content, only succeeded in blocking around a third of ads — a stark contrast to competitors like Avira, which managed to block almost all ads.
Malwarebytes also offers Identity Theft Protection services, but this is a separate offering at a much higher price point, starting at $99.99 / year. However, if you sign up for one of the ID Theft Protection plans, you also get Malwarebytes Plus, which includes the antivirus, Browser Guard, and VPN, which is great.
Unfortunately, Malwarebytes doesn’t have some of the additional features that the other antiviruses on this list offer (like a firewall, PC optimization tools, parental controls, etc.). While I’d like to see Malwarebytes add some of these extra features, I still think it’s a pretty good choice for users looking for a decent antivirus program that they can install and forget about. Malwarebytes starts at $59.99 / year.
Bottom Line:
Malwarebytes is a straightforward and minimalistic antivirus program, offering effective malware scanning and web protection. It provides a reliable VPN and user-friendly interface, and it offers comprehensive Identity Theft Protection (though this isn’t included in its standard antivirus packages). Despite some limitations in features like ad-blocking, Malwarebytes is a solid choice for those seeking basic, no-frills virus protection. Malwarebytes comes with a generous 60-day money-back guarantee.
Read the full Malwarebytes review here >
Bonus. MacKeeper — Intuitive & Feature-Rich Antivirus for Mac
MacKeeper is one of the rare antiviruses specifically designed for Mac — and it comes with good malware protection, a range of security and privacy features that build upon Apple’s native protections, and a very intuitive macOS app.
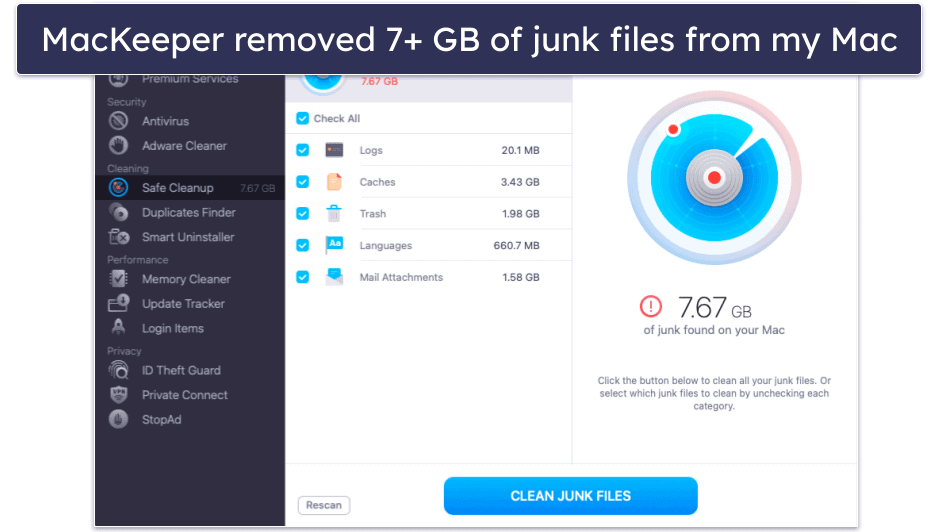
In my testing, MacKeeper detected over 99% of Mac-specific malware files, which is similar to the best antiviruses for Mac, including Intego and McAfee. And its Mac cleanup and optimization tools removed around 7 GB of junk and duplicate files from my MacBook Pro (I also really like how MacKeeper offers the option to delete unwanted email attachments, which is something I haven’t seen in any other antivirus).
MacKeeper’s VPN is also really good — secure, fast, and compatible with most streaming sites. The only thing I dislike about the VPN is the lack of transparency regarding the no-logs policy, so I’d like to see MacKeeper provide clearer information on how it manages user data.
On the other hand, MacKeeper is missing anti-phishing protection, which I consider to be a crucial security feature for an antivirus in 2024. It also doesn’t have a firewall or parental controls, both of which are included with Intego.
MacKeeper offers several plans that start at $10.95 / month. The plans are all the same, and the only difference between them is in the length of the subscription and the number of Mac computers covered (1–3).
Bottom Line:
MacKeeper is a really good Mac-only antivirus — it has near-perfect malware detection rates, it includes excellent system cleanup tools, and it offers a secure and fast VPN with unlimited data. However, it’s missing anti-phishing protection, a firewall, and parental controls. MacKeeper offers several paid plans and backs all purchases with a 14-day money-back guarantee.
Read the full MacKeeper review here >
Quick Comparison Table
Testing Methodology: Comparison & Ranking Criteria
When rating products, I followed our tried and tested methodology. I ran real-life scenarios with criteria that included checking security, speed, ease of use, value, and customer support. In particular:
- I tested malware detection rates and scanning capabilities. I conducted dozens of malware tests, real-time protection tests, CPU performance tests, and more. I did this to ensure each of these products provided rock-solid protection against all viruses, malware, and other dangerous internet security threats. Once done, only the products that protected against the most advanced malware threats made it to this list — these products not only detect and remove viruses but also tackle spyware, rootkits, ransomware, and anything else that could cause me or my devices harm. Norton and Bitdefender did the best here, but the other antiviruses on this list performed well, too.
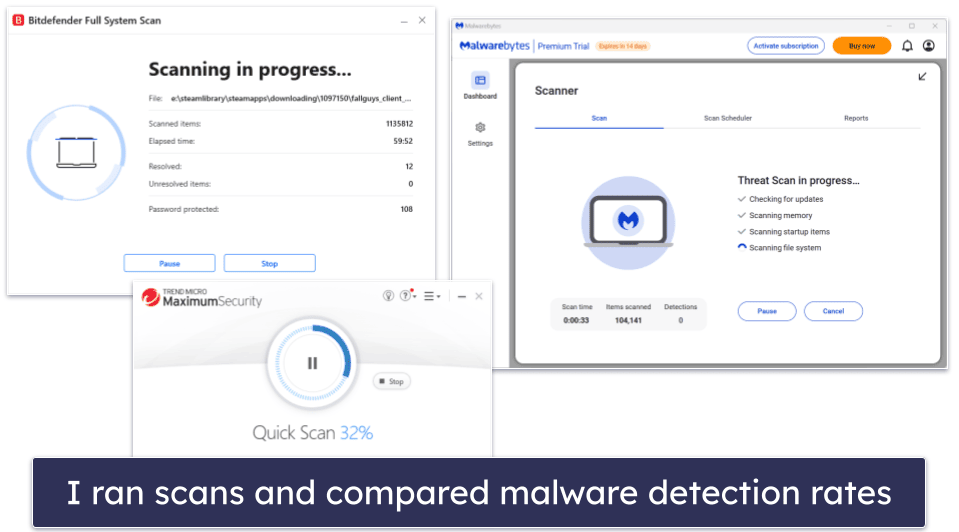
- I counted the number of false positives. While no antivirus is 100% immune to false positives, some programs raise fewer false positives than others — I still think it’s better for an antivirus to raise false positives than to miss real malware, but constantly getting false alerts can be pretty annoying. The antiviruses on this list returned zero or very few false positives during my tests.
- I looked for high-quality features. Most antivirus brands offer additional features in their paid antivirus packages. But often these extras are just flashy additions that weigh your computer down and affect your device’s performance (not to mention increase the price). I tested each of the features included with the products on this list to guarantee that they’re genuinely useful and effective. Bitdefender has the biggest range of helpful features, but TotalAV comes with excellent tune-up tools.
- I tested for speed and efficiency. The best antiviruses are lightweight and run smoothly — even on older or slower computers. I tested and measured how quickly and efficiently each antivirus on this list performed against all the other antiviruses on the market and awarded extra points to those that didn’t cause any slowdown.
- I checked for multi-platform support. The top antiviruses are compatible with all operating systems, including popular ones like Windows, macOS, Android, and iOS. While not all of my top choices support all platforms (for example, Intego is designed exclusively for Mac), most antiviruses I tested worked flawlessly across all operating systems.
- I contacted customer support multiple times. I contacted each company’s customer support team, browsed their knowledge bases, and posted questions on their forums. I was satisfied with how each antivirus on this list handled my inquiries and resolved my issues. I also looked at the different customer support options available and the number of languages they’re accessible in — the brands on this list offer a wide range of customer support options, including live chat, email support, knowledge bases, FAQs, and forums.
- I evaluated the value of each product. Antivirus software can be a big investment. I considered all relevant factors, such as web and browsing protection, how many devices are covered, and whether or not there’s a free trial or money-back guarantee. All of these top antiviruses provide great value.
How to Choose the Best Antivirus for Your Operating System
Choosing the best antivirus for your operating system is similar to choosing the best antivirus in general: you should pay attention to its features, performance impact, ease of use, detection rates, quality of customer support, and pricing. However, there are also two additional points to consider:
- Identify your operating system’s specific needs. For example, Windows is the OS that’s most often targeted by cyberattacks thanks to its widespread use. When seeking to protect a Windows device, look for an antivirus with a strong track record of Windows protection (like Norton). The same applies to macOS — while it’s less frequently targeted than Windows, threats are increasing. Choose antivirus software that specializes in detecting macOS-specific malware (like Intego).
- Check compatibility. Ensure the antivirus software is fully compatible with your OS version to avoid performance issues. For instance, if you’re on an older computer, try to pick an antivirus like Bitdefender that operates in the cloud.
I can honestly recommend Norton as the best overall antivirus in 2024, having stress-tested all of the programs on this list on all of the most popular operating systems. In addition to having perfect malware detection rates and a comprehensive set of internet security tools, Norton provides well-designed, intuitive apps for Windows, Android, Mac, and iOS. While it doesn’t have an app for Chrome OS, its Android app also works on Chromebooks (and it’s our #1 choice for Chromebook protection).
You may also wish to take a look at our curated lists of the best antiviruses for different operating systems and devices below:
- Best antiviruses for Windows. Most antivirus brands have the best protections for Windows devices, so choosing the best Windows antivirus can be difficult. But after extensive research, testing, and comparing, we recommend Norton as the top pick for Windows 8, 10, and 11.
- Best antiviruses for Mac. Unfortunately, because most antiviruses focus on Windows, a lot of them provide only bare-bones versions of their Windows software for Mac users. However, there are several really good macOS antiviruses that provide good malware protection, improve upon Apple’s built-in protections, and are easy to use on Mac devices. Our top choice for macOS is Intego.
- Best antiviruses for Android. Many Android antiviruses aren’t good enough to fully protect your device from the latest internet threats, but there are a handful of apps that provide excellent malware and web protection, as well as extras that can further secure your online activities. We recommend Norton or Bitdefender as the top Android antiviruses.
- Best antiviruses for iOS. While it’s true that iOS devices can’t get viruses, they are vulnerable to a wide range of online threats, including phishing scams, spyware and adware, and identity theft. The best iOS antiviruses can keep your device and data safe from all of these threats. Our #1 antivirus for iOS is Norton.
Quick Guide: How to Use an Antivirus
- Install from a reputable source. Navigate to the official website or a verified retailer of your chosen antivirus to ensure you’re getting a genuine copy. Since Norton is my top pick, I’ll use it as an example here.
- Choose a plan that suits your needs. Review all the plans on offer by your antivirus provider to find the best one for you. Don’t forget to look for a money-back guarantee (Norton, for example, offers a 60-day money-back guarantee on all of its plans).
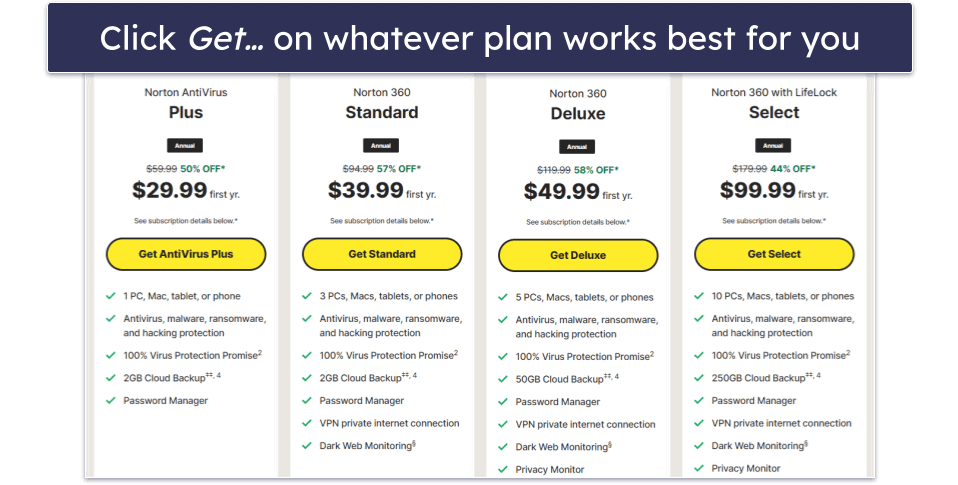
- Set up your account. Once you’ve chosen and purchased a subscription, it’s time to register with the antivirus provider. Provide your details and click Create Account.

- Perform an initial full system scan. Download and install your antivirus software, then run a full system scan to check for any existing threats on your device. This may take some time, but it’s crucial for starting with a clean slate.
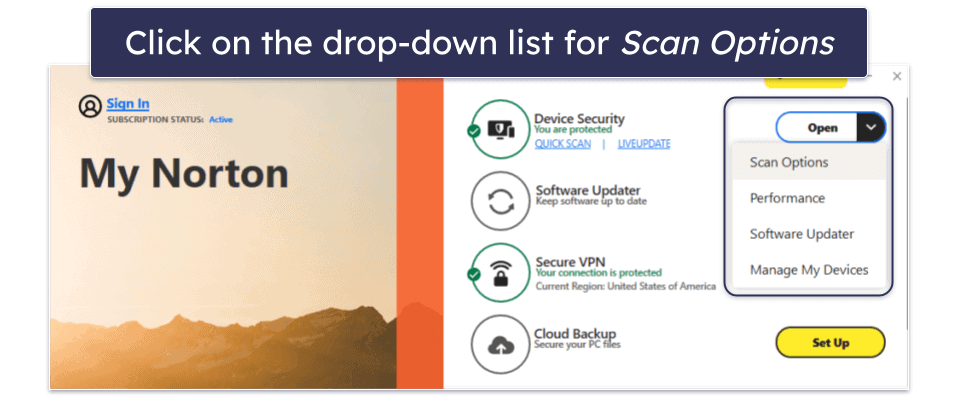
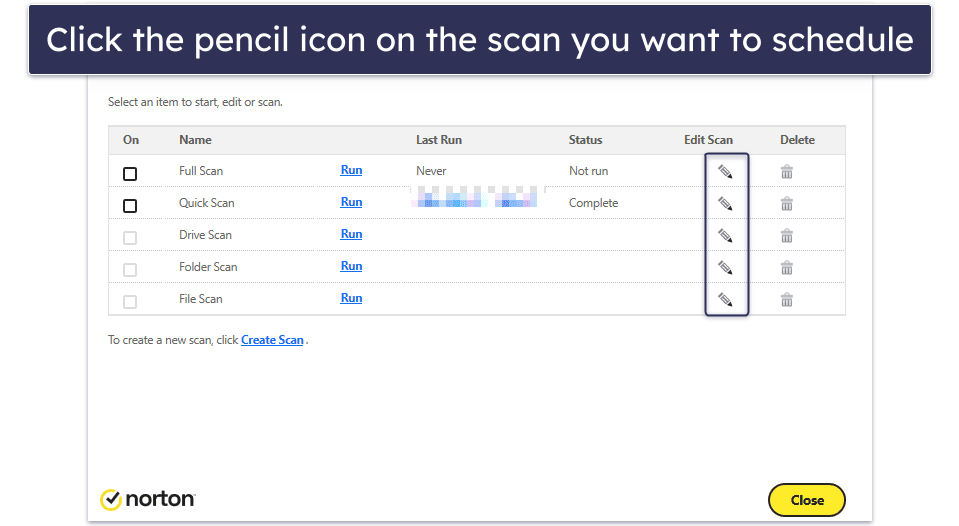
- Schedule regular scans. Besides real-time protection (turned on by default in Norton), schedule regular full system scans (e.g., weekly or monthly) to consistently search for any malware that might have slipped through.
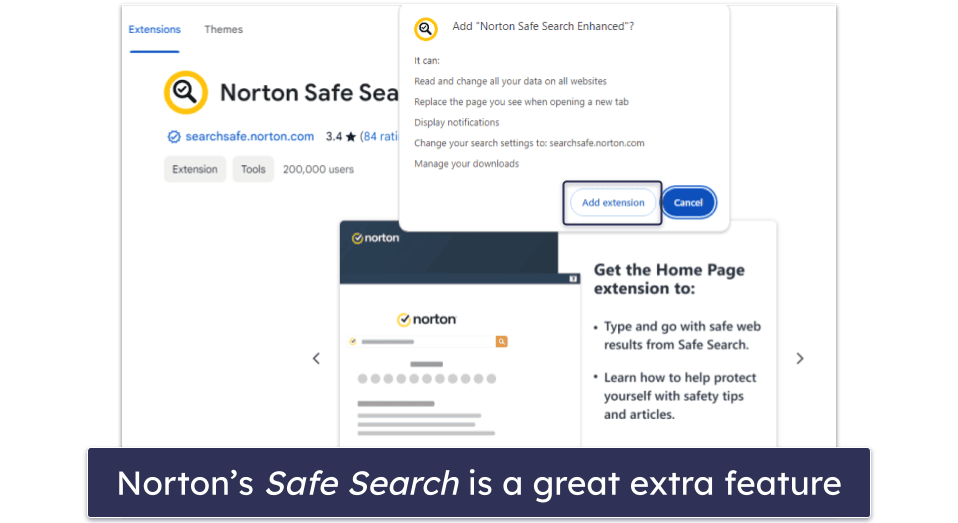
- Use additional security features. Explore and utilize additional features offered by your antivirus, such as a firewall, web protection, anti-phishing, and parental controls. Norton, for example, has an excellent browser extension, Norton Safe Web, which you can install to enhance your online security.
- Stay informed about new features. Periodically review your antivirus software’s documentation or news updates to learn about new features or settings that can improve protection. Norton’s official website, for example, features a dedicated product & service announcement blog, where you can read all about the latest updates to its antivirus program.
Following these steps will help you maximize the effectiveness of your antivirus software, keeping your digital environment secure against a wide range of cyber threats.
Built-In vs. Third-Party Antiviruses — Which Is Better?
A reliable third-party antivirus is a better option. The built-in protections of Mac and Windows operating systems cannot match the comprehensive security offered by a premium antivirus solution. While the basic free protections provided by these systems are a good start, they don’t offer sufficient defense against advanced threats in 2024.
If you’re a Windows user, you’ll have Windows Defender on your computer (newer Windows 10 and 11 computers call it Windows Security or Microsoft Defender). While it’s a decent free antivirus, it scores consistently lower for malware detection than top standalone brands like Norton and Bitdefender. What’s more, it doesn’t get updated as regularly as premium standalone products, and it lacks all the additional security tools that a good paid antivirus can provide, such as a VPN, performance optimization tools, a password manager, and more.
Instead, I recommend investing in a premium antivirus like Norton to keep yourself safe online. It has a comprehensive suite of tools to ensure your security — including the best dark web monitoring on the market. However, if you’re set on using a free product, a decent free plan like Avira’s will also keep you safer than Windows Defender can.
Macs are less vulnerable to malware than Windows PCs — but they still need protection! Macs come with a few built-in security features, including web protection, anti-theft tools, an app review tool, and an app scanner. These are useful enough, but on their own they’re not enough to keep you safe. Your Mac could still be vulnerable to advanced ransomware, spyware, adware, and other threats.
For enhanced protection on Mac, consider using a premium Mac-specific antivirus such as Intego. It provides impeccable malware detection, effective Mac cleanup tools, parental controls, and numerous other features.
Overall, it’s not wise to rely on your computer’s in-built protections. Instead, choose a reliable premium antivirus to keep you fully protected online. Any of the products on my list will give you better protection than Windows’s and Mac’s in-built tools can.
What Security Threats Can an Antivirus Protect You Against?
A quality antivirus provides strong protection against most security threats.
Here are the most common forms of malware that antiviruses defend against:
- Viruses. A type of malware that can self-replicate and make unauthorized (and malicious) changes to your computer. These are reliably detected and quarantined by premium antiviruses.
- Potentially Unwanted Programs (PUPs). PUPs are a type of software that can modify your browser settings and fill your screen with ads. They aren’t necessarily malicious or illegal, but they tend to be annoying and invasive.
- Adware. If you’re seeing an uptick in ads, adware could be the cause. Adware is a type of malware that drowns you in advertisements. They can interfere with your device even when you’re not connected to the internet, causing frustration and collecting data.
- Spyware. A general term for malware designed to acquire sensitive information about the victim. In the best scenario, a spyware infection could lead to eerily targeted ads. But often the situation is much worse, with keyloggers (a type of spyware) stealing passwords and other personal information to sell to third parties.
- Trojans. Arguably the most dangerous type of malware, trojans are viruses that initially appear to be normal programs. But after certain conditions are met, they begin acting maliciously, replicating themselves across your network, stealing data, and damaging devices.
- Worms. Worms are viruses that automatically spread, infecting everything they can. Unlike trojans, they cause damage immediately. This could involve corrupting files, operating systems, or spamming annoying messages.
- Ransomware. A type of malware that encrypts files to hold for ransom — ransomware will display a message with instructions about what you need to do to regain control of your device. The best defense is an antivirus with ransomware remediation (such as Bitdefender) that will halt the encryption process, as there’s no guarantee that cybercriminals will relinquish control even if they’ve been paid.
- Rootkits. Rootkits are a particularly dangerous type of malware that can seize administrator privileges and otherwise make critical changes to computers.
- Browser exploits. A good antivirus (like the ones on this list) will automatically detect suspicious activity in your browser, preventing hackers from using vulnerabilities to change your browser’s settings or perform other malicious actions.
- Phishing attempts. Phishing is a method that criminals use to steal personal information and take over accounts. Antiviruses are built to detect web-based phishing attempts, usually through databases of malicious websites.
In essence, antiviruses guard against all key online threats, and the top ones are incredibly successful in fulfilling this role. However, it’s crucial to keep in mind that nothing is flawless – even when equipped with the best antivirus, you must still exercise caution online.
Why We Still Recommend Kaspersky
The German and US governments have warned against using Kaspersky, following the Russian invasion of Ukraine in February 2022. Germany’s Federal Office for Information Security (BSI) warned companies against using Kaspersky antivirus products due to the company’s possible ties to the Russian government. This was followed by the US Federal Communications Commission’s decision to add Kaspersky to its list of national security threats.
However, at this point, there is no evidence to suggest Kaspersky is unsafe. In 2017, Kaspersky started its Global Transparency Initiative — it moved its data storage centers to Switzerland, opened Transparency Centers in Switzerland, Spain, Canada, Brazil, and Malaysia where its source code and software updates are continually assessed, and passed the Service Organization Control for Service Organizations (SOC 2) Type 1 audit.
What’s more, Kaspersky has exposed many cases of cyber espionage, including those perpetrated by both Russia and the US, and its researchers are among the most well-respected in the industry.
Given all this, we have no reason to think Kaspersky is now a threat to users. But if you’re worried about Kaspersky putting your online security at risk, there are many other alternatives to choose from, including Norton or Bitdefender.
Top Brands That Didn’t Make the Cut:
- ESET. ESET makes great contributions to the field of cybersecurity. Unfortunately, its current home antivirus product is not user-friendly enough for me to put it on this list.
- Webroot. Webroot is a lightweight program with a good malware scanner and an excellent password manager, but its ransomware protection isn’t great, its system optimization tools need improvement, and it’s missing most of the extras I want to see in a premium antivirus in 2024.
- Sophos. Sophos is good at detecting all types of malware, its apps are very easy to use, and it has remote management for up to 10 devices. However, I don’t like its additional features, and I think the brands that made it to my list offer an overall better value.
- Heimdal. Heimdal is a decent antivirus with a good firewall and advanced inspection features. Unfortunately, it has some annoying bugs and offers fewer security features than similarly-priced competitors on this list.
- Comodo. Comodo is a free antivirus with decent malware removal rates, but its cross-platform antivirus product currently has too many bugs, and certain features don’t work properly.
- AVG. AVG has perfect malware detection rates and a good range of additional features. However, you need 6 separate apps to access every feature, which slowed down my computer’s startup time.
- Avast. Avast offers decent antivirus protection, but it has limited data breach monitoring and a mediocre VPN.
- G Data. G Data offers solid antivirus protection and a user-friendly interface. However, its phishing protection needs strengthening. It also lacks additional features like an integrated VPN and advanced parental controls.
Frequently Asked Questions
What are viruses and malware?
Viruses and malware are terms for threats that damage devices, steal information, or otherwise inconvenience the user. Viruses take the form of malicious self-replicating software, while malware is a more general term that covers any software designed to cause harm. There are many types of malware and viruses that fall into different categories and act in different ways to accomplish various malicious objectives. For victims of malware and viruses, this can mean anything from being bombarded with ads to having critical financial and personal information stolen.
Ultimately, viruses and malware are digital traps laid by criminals to make money or frustrate others. They take many forms, and all of them are bad.
What are some features an antivirus should have?
A good antivirus should protect you against numerous digital threats while being user-friendly. Here’s a rundown of key features to look for:
Essential features:
- Malware detection & removal: Effective against a variety of malware types.
- Real-time protection: Stops infections before they cause harm.
- Regular updates: Keeps up with new threats.
- Ease of use: Has a user-friendly interface and setup.
- Low system impact: Operates smoothly without slowing down your device.
Advanced features:
- Firewall: Monitors network traffic to block unauthorized access.
- VPN: Provides privacy and security online.
- Password manager: Assists in managing strong, unique passwords.
- Parental controls: Safeguard children’s online activities.
- Identity theft protection: Protects personal and financial information.
- System optimization tools: Helps maintain device performance.
- Data backup & recovery: Secures important data against loss.
How does an antivirus work?
Antivirus software scans your device for any harmful files. These harmful files are known as viruses or malware — and they include a wide range of different threats, like trojans, worms, spyware, adware, keyloggers, cryptojackers, rootkits, and more. In most cases, malware is designed to damage your device or gain access to your sensitive data for financial gain — or both.
Antivirus programs use malware databases to see if the code of any of your scanned files matches the code of known malware in the database. They also check for files that are similar to the ones in the database. Advanced programs like Norton also use machine learning to detect malware based on their behavior. This is how antivirus software is able to detect new or emerging malware.
In addition to providing an on-demand malware scanner that detects and removes malware that has already infected your system, antivirus software also includes real-time protection that actively scans the programs that are running in real-time. Real-time protection is therefore able to block malware BEFORE it can infect your device.
What’s the best antivirus software for Windows 10?
I recommend Norton 360 as the best antivirus for most Windows 10 users. It provides the best antivirus protection according to my tests, and it includes some excellent extra features — phishing protection, Wi-Fi protection, a password manager, a firewall, a VPN, and a lot more.
But all of the antiviruses on this list will work for all Windows 10 users (and many even work on older PCs that run on Windows 7 and Windows XP).
What’s the best antivirus with a firewall?
In my opinion, Norton is the best antivirus that includes a firewall. It has lots of excellent security features, of which the firewall is just one. It’s earned its position at the top of this list thanks to its perfect malware detection rates and other useful features, all of which are easy to use. The firewall is highly customizable, meaning it’s great for experts and beginners alike. It’s also super effective, providing ARP and DNS spoofing protection, SSL man-in-the-middle attack detection, and port access detection.
Do I really need an antivirus in 2024?
If you’re using the internet, you need to stay protected against online threats. The good news is that you’re probably already using an antivirus — if you’re on Windows, Mac, or mobile OS, your devices already have antivirus protection. And these built-in antiviruses are not bad. But they do leave a lot of holes in your cybersecurity.
The top antivirus packages all offer advanced protections — full-suite anti-malware engines (including phishing protection, ransomware protection, webcam protection, and Wi-Fi protection), security enhancements (including customizable firewalls, parental controls, and device optimization), and extra features (like password managers, file shredders, and VPNs). Norton 360 and Bitdefender Total Security both have all of these things and more.
So the question of buying an antivirus isn’t so much about if you need it — because you do — but it’s more about what level of protection you want to have.
Is it worth paying for antivirus software?
Yes. While free antivirus software, including Windows Defender that’s built into all PCs, has greatly improved over the years, it still lacks many protections necessary for complete online security in 2024.
For example, most free antiviruses lack real-time protection, which prevents malware from installing on your device while you’re using your computer. Free products also lock some of their most useful features behind a paywall, such as ransomware protection, web protection, or virtual private networks (VPNs).
The best paid antiviruses, on the other hand, include all of these features, plus many other extras (like password managers, parental controls, and system optimization tools). Premium antiviruses like Norton also include multi-device coverage across all major operating systems so you can protect all of the devices in your household.
How much does a good antivirus cost?
A decent antivirus doesn’t cost much at all, especially considering the protection one offers.
For example, Norton, our top-rated antivirus, starts at just $54.99 / year*. You can also pay a little extra to upgrade your plan to cover all of your devices and to access more features, such as dark web monitoring, a VPN, and identity theft protection.
However, some antivirus products are far too expensive and don’t provide good-quality features, so it’s always best to look for antiviruses that offer a good value for the price.
What’s the best antivirus for ransomware protection?
I think that Norton provides the best defense against ransomware. I say this based on my own tests and first-hand knowledge of Data Protector, Norton’s anti-ransomware feature. It’s a highly customizable tool that actively defends against ransomware by closely monitoring what’s going on with your files. I found that even after whitelisting a ransomware simulator through the Norton app, Norton still stopped it from encrypting my files. I haven’t tested any antivirus that scored a higher ransomware detection rate than Norton.
What is the cheapest antivirus software?
Bitdefender is one of the cheapest antiviruses on the market, starting at just $17.49 / year, and it also offers some of the best security features around.
However, most top antivirus brands regularly run special promotional offers, significantly reducing their price per subscription (for example, Norton is currently offering a 58% discount, so its plans start at just $54.99 / year*).
It’s worth noting that some cheap (and free) antiviruses don’t offer a decent level of protection, so while you may be saving money, you could put your devices at risk. That’s why you should only choose a trusted low-cost antivirus that offers excellent security protections.
What’s the best antivirus software for Mac?
I recommend Intego as the best antivirus for Mac. It’s designed exclusively for macOS, and it performed exceptionally well in my tests. It’s got a lot of cool features like real-time protection and a customizable network firewall.
That said, most of the antivirus products on this list have highly capable Mac applications as well. And they all run without any issues, even though there may be certain conditions.
For example, Norton 360 is a great choice for Mac users, but certain features (such as Cloud Backup and Parental Control) are limited on Mac due to Apple’s restrictions.
Can I have more than 1 antivirus on my computer?
Though it’s possible, I don’t recommend running more than 1 antivirus at a time. When multiple antiviruses are active on the same system, they interfere with each other, making it easier for viruses and other threats to slip past your computer’s defenses. There are lots of great antiviruses to pick, and you won’t ever need more than one of them.
Do phones need an antivirus?
Yes, they do. Whether you have an iPhone or an Android, it’s always a good idea to protect your phone with an antivirus. Though the specific nature of the threats is different compared to computers, mobile devices are great targets for cybercriminals. Phishing is a common problem on Android and iOS, and there are many viruses that can compromise Android phones. Some of the brands on this list have mobile versions, but I recommend checking out our dedicated pages for iPhones and Android devices.
How to install an antivirus?
Installing an antivirus is pretty easy — much easier than fixing a virus-infested computer. All you need to do is pick an antivirus like Norton, download the software, and run the installation wizard. As you’re going through the installation wizard, read the instructions carefully — some antiviruses like to package additional software in their installations that you don’t really need. Once done, the antivirus software will start automatically and provide you with a tour of its user interface, instructing you how to run your initial scan.
How do I choose the best antivirus software for me?
Choosing the right antivirus software package can be challenging — there are so many choices, and the most expensive products don’t always offer the best protection.
Here’s what you should do to help you find the right antivirus product:
- Decide what features you need. Basic antivirus protection is essential, but other internet security features are also important. If you use public Wi-Fi networks, you should choose a product that includes a VPN. If you have kids, you should find an antivirus with parental controls. The more comprehensive products on this list, such as Norton 360, provide these advanced features (and a lot more).
- Consider which and how many devices you need to protect. You might have more than one device that requires antivirus protection. All the products on this list offer plans with multiple licenses — for example, you can use the top McAfee plan on an unlimited number of devices, including smartphones. While most of my top choices also offer top-quality apps for all major operating systems, including Windows, macOS, Android, and iOS, some antiviruses don’t have mobile apps — for example, Intego doesn’t have an app for iOS or Android, but it’s my top recommendation for macOS.
- Take advantage of a free trial/money-back guarantee. There are several brands on this list that offer a no-commitment free trial. For example, your first month using Panda is totally free. And almost every other brand offers a “no questions asked” money-back guarantee — for example, TotalAV offers a 30-day refund period, and Norton’s refund period is a generous 60 days.
- Test out the software. Spend some time testing the product you’ve chosen. If you’re not happy, reach out to customer support. Or simply get a refund — these brands have seriously good reputations to maintain, and they will 100% honor any valid refund request. You could conceivably test every product on this list — at no expense whatsoever — before settling on the right one.
Will an antivirus slow down my device?
Antivirus software may slow down your device — but system slowdown usually happens only during a full system scan. However, the best antivirus programs run quickly and smoothly even during full scans, allowing you to uninterruptedly use your device.
My top choices, Norton and Bitdefender, had zero impact on my device’s performance during testing — I could stream video, play games, work online, and make video calls while they were running in the background.
Additionally, some of my top choices have excellent system optimization tools that will help clean and speed up your device. And some brands even include game boosters (I recommend Norton for gamers), which enable you to play high-performance games without any lag.
